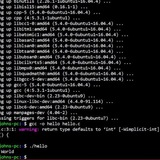
TUI File Manager in Bash
https://preview.redd.it/ao14kf51nh1g1.png?width=1914&format=png&auto=webp&s=647a8623a329e0ac3f61e241b04c40f2736b43f2
Checkout this file manager i made in pure bash
Do give a star if you like it - https://github.com/Aarnya-Jain/bashfm
https://redd.it/1oy3chh
@r_bash
https://preview.redd.it/ao14kf51nh1g1.png?width=1914&format=png&auto=webp&s=647a8623a329e0ac3f61e241b04c40f2736b43f2
Checkout this file manager i made in pure bash
Do give a star if you like it - https://github.com/Aarnya-Jain/bashfm
https://redd.it/1oy3chh
@r_bash
Accidentally created an emotional OS
\#!/usr/bin/env bash
\# feralChurchBasementOS.sh
\# emotional maintenance noscript for unstable human systems
set -euo pipefail
OS_NAME="feralChurchBasementOS"
VERSION="v1.0"
log() {
printf "[%s\] %s\\n" "$(date +'%Y-%m-%d %H:%M:%S')" "$*"
}
uninstall_shame() {
log "Purging inherited shame..."
\# placeholder for actual work
sleep 1
log "Shame removed from user-space (may respawn, monitor with journalctl)."
}
reboot_self_worth() {
log "Rebooting self-worth service..."
\# simulate stop/start
sleep 1
log "self-worth.service is now active (running)."
}
patch_trauma_kernel() {
log "Applying trauma kernel patches..."
\# pretend to apply updates
sleep 1
log "Kernel patched. Reboot recommended for changes to take full effect."
}
close_background_processes() {
log "Scanning for emotional background processes..."
\# pretend to kill runaway processes
sleep 1
log "Terminated: overthinking, catastrophizing, people-pleasing."
}
restrict_root_access() {
log "Hardening permissions on /home/heart..."
\# pretend to change ownership/permissions
sleep 1
log "Root access to feelings restricted. Sudo now requires consent."
}
run_health_check() {
log "Running post-maintenance health check..."
sleep 1
log "System status: degraded but functional (expected)."
}
main() {
log "Initializing ${OS_NAME} ${VERSION}..."
uninstall_shame
reboot_self_worth
patch_trauma_kernel
close_background_processes
restrict_root_access
run_health_check
log "Done. For ongoing maintenance, schedule via cron:"
log " 0 3 * * * ${PWD}/feralChurchBasementOS.sh >/var/log/basementOS.log 2>&1"
log "Manual override available with: sudo apt-get heal"
}
main "$@"
https://redd.it/1oyqzgo
@r_bash
\#!/usr/bin/env bash
\# feralChurchBasementOS.sh
\# emotional maintenance noscript for unstable human systems
set -euo pipefail
OS_NAME="feralChurchBasementOS"
VERSION="v1.0"
log() {
printf "[%s\] %s\\n" "$(date +'%Y-%m-%d %H:%M:%S')" "$*"
}
uninstall_shame() {
log "Purging inherited shame..."
\# placeholder for actual work
sleep 1
log "Shame removed from user-space (may respawn, monitor with journalctl)."
}
reboot_self_worth() {
log "Rebooting self-worth service..."
\# simulate stop/start
sleep 1
log "self-worth.service is now active (running)."
}
patch_trauma_kernel() {
log "Applying trauma kernel patches..."
\# pretend to apply updates
sleep 1
log "Kernel patched. Reboot recommended for changes to take full effect."
}
close_background_processes() {
log "Scanning for emotional background processes..."
\# pretend to kill runaway processes
sleep 1
log "Terminated: overthinking, catastrophizing, people-pleasing."
}
restrict_root_access() {
log "Hardening permissions on /home/heart..."
\# pretend to change ownership/permissions
sleep 1
log "Root access to feelings restricted. Sudo now requires consent."
}
run_health_check() {
log "Running post-maintenance health check..."
sleep 1
log "System status: degraded but functional (expected)."
}
main() {
log "Initializing ${OS_NAME} ${VERSION}..."
uninstall_shame
reboot_self_worth
patch_trauma_kernel
close_background_processes
restrict_root_access
run_health_check
log "Done. For ongoing maintenance, schedule via cron:"
log " 0 3 * * * ${PWD}/feralChurchBasementOS.sh >/var/log/basementOS.log 2>&1"
log "Manual override available with: sudo apt-get heal"
}
main "$@"
https://redd.it/1oyqzgo
@r_bash
Script to re-assemble HTML email chopped up by fetchmail/procmail
I use "fetchmail" to pull down email via POP3, with "procmail" handling delivery, and "mutt" as my mailreader. Long lines in emails are split and wrapped. Sometimes I get a web page as an email for authentication. Usually the first 74 characters of each long line are as-is, followed by "=" followed by newline followed by the rest of the line. If the line is really long, it'll get chopped into multiple lines. Sometimes, it's 75-character-chunks of the line followed by "=".
I can re-assemble the original webpage-email manually with vim, but it's a long, painfull, error-prone process. I came up with the following noscript to do it for me. I call the noscript "em2html". It requires exactly 2 input parameters...
- the original raw email file name
- the desired output file name, to open with a web browser. The name should have a ".htm" or ".html" extension so that a web browser can open it.
Once you have the output file, open it locally with a web browser. I had originally intended to "echo" directly to the final output file, and edit in place with "ed", but "ed" is not included in my distro, and possibly yours. Therefore I use "mktemp" to create an interim scratch file. I have not yet developed an algorithm to remove email headers, without risking removing too much. Here's the noscript...
~~~
#!/bin/bash
if ${#} -ne 2 ; then
echo 'ERROR The noscript requires exactly 2 parameters, namely'
echo 'the input file name and the output file name. It is recommended'
echo 'that the output file name have a ".htm" or ".html" extension'
echo 'so that it is treated as an HTML file.'
exit
fi
tempfile="$(mktemp)"
while read
do
if "${REPLY: -1}" = "=" ; then
xlength=$(( ${#REPLY} - 1 ))
echo -n "${REPLY:0:${xlength}}" >> "${tempfile}"
else
echo "${REPLY}" >> "${tempfile}"
fi
done<"${1}"
sed "s/=09/\t/g
s/=3D/=/g" "${tempfile}" > "${2}"
rm -rf "${tempfile}"
~~~
https://redd.it/1ozghjm
@r_bash
I use "fetchmail" to pull down email via POP3, with "procmail" handling delivery, and "mutt" as my mailreader. Long lines in emails are split and wrapped. Sometimes I get a web page as an email for authentication. Usually the first 74 characters of each long line are as-is, followed by "=" followed by newline followed by the rest of the line. If the line is really long, it'll get chopped into multiple lines. Sometimes, it's 75-character-chunks of the line followed by "=".
I can re-assemble the original webpage-email manually with vim, but it's a long, painfull, error-prone process. I came up with the following noscript to do it for me. I call the noscript "em2html". It requires exactly 2 input parameters...
- the original raw email file name
- the desired output file name, to open with a web browser. The name should have a ".htm" or ".html" extension so that a web browser can open it.
Once you have the output file, open it locally with a web browser. I had originally intended to "echo" directly to the final output file, and edit in place with "ed", but "ed" is not included in my distro, and possibly yours. Therefore I use "mktemp" to create an interim scratch file. I have not yet developed an algorithm to remove email headers, without risking removing too much. Here's the noscript...
~~~
#!/bin/bash
if ${#} -ne 2 ; then
echo 'ERROR The noscript requires exactly 2 parameters, namely'
echo 'the input file name and the output file name. It is recommended'
echo 'that the output file name have a ".htm" or ".html" extension'
echo 'so that it is treated as an HTML file.'
exit
fi
tempfile="$(mktemp)"
while read
do
if "${REPLY: -1}" = "=" ; then
xlength=$(( ${#REPLY} - 1 ))
echo -n "${REPLY:0:${xlength}}" >> "${tempfile}"
else
echo "${REPLY}" >> "${tempfile}"
fi
done<"${1}"
sed "s/=09/\t/g
s/=3D/=/g" "${tempfile}" > "${2}"
rm -rf "${tempfile}"
~~~
https://redd.it/1ozghjm
@r_bash
Reddit
From the bash community on Reddit
Explore this post and more from the bash community
New Project: “GeoBlocker” — US-only SSH Geo-fencing with nftables (feedback welcome!)
https://redd.it/1p05fuu
@r_bash
https://redd.it/1p05fuu
@r_bash
Reddit
From the bash community on Reddit
Explore this post and more from the bash community
imgur album fetcher
I'll just leave this here:
for x in $(curl https://imgur.com/gallery/ultimate-4k-wallpaper-dump-2-cats-8Yxub | awk -F 'window.postDataJSON="' '{print $2}' | awk -F '"</noscript>' '{print $1}' | sed 's/\\//g' | jq '.media.[].url' | sed 's/"//g'); do timeout 5 curl "$x" > "${x##*/}"; done
https://redd.it/1p0nbii
@r_bash
I'll just leave this here:
for x in $(curl https://imgur.com/gallery/ultimate-4k-wallpaper-dump-2-cats-8Yxub | awk -F 'window.postDataJSON="' '{print $2}' | awk -F '"</noscript>' '{print $1}' | sed 's/\\//g' | jq '.media.[].url' | sed 's/"//g'); do timeout 5 curl "$x" > "${x##*/}"; done
https://redd.it/1p0nbii
@r_bash
New Project: “GeoBlocker” — US-only SSH Geo-fencing with nftables (feedback welcome!)
Hey everyone,
I’m pretty new to sharing code publicly, so please be gentle 😅 — but I’ve been working on something I think could be useful to others, and I’d love feedback from people far more experienced than me.
# 🔒 What is GeoBlocker?
GeoBlocker is a Bash-based tool for Ubuntu 24.04 servers that want to lock down SSH (port 22) to US IP ranges only, using fast-loading nftables sets and geo-IP lists from IPdeny.
Features:
Fetches US IPv4 + IPv6 ranges (with IPdeny usage-limits respected)
Bulk-loads them efficiently into nftables sets (avoiding slow “one CIDR at a time” loops)
Optional SSH whitelist (IPv4 + IPv6)
Investigation mode that shows:
nftables status
whitelist status
SSH client IP
privileges
missing sets or config issues
Backup + atomic write safety
Nothing applied automatically — you stay in control of `/etc/nftables.conf`
Repo is here:
👉 [https://github.com/baerrs/GeoBlocker](https://github.com/baerrs/GeoBlocker)
# 🛠️ Why I built it
I run a small personal server and kept seeing tons of SSH brute-force attempts from around the world.
Fail2ban helped, but I wanted a stronger approach: just block every non-US address before they even reach SSH.
I found a lot of half-solutions or outdated guides, so I wrote a noscript that:
is reproducible
uses best practices
keeps nftables clean
and is safe for beginners (backups, dry-run behavior, etc.)
# 🙋♂️ What I want feedback on
Since I’m new to publishing open-source noscripts:
Is the structure reasonable?
Any obvious improvements to safety, portability, or code style?
Is the README clear enough?
Any red flags for production usage?
Suggestions for features? (cron auto-update? IPv4/v6 country selection? Better logging?)
I’m totally open to constructive criticism — just keep in mind I’m still learning how to present and share code. ❤️
# Thanks in advance!
If anyone has ideas, corrections, or wants to help evolve the project, I’d really appreciate it.
And if even one person finds it useful, that’s a big win for me already.
Thanks! 🙏
— Scott (R. Scott Baer)
https://redd.it/1p11m9l
@r_bash
Hey everyone,
I’m pretty new to sharing code publicly, so please be gentle 😅 — but I’ve been working on something I think could be useful to others, and I’d love feedback from people far more experienced than me.
# 🔒 What is GeoBlocker?
GeoBlocker is a Bash-based tool for Ubuntu 24.04 servers that want to lock down SSH (port 22) to US IP ranges only, using fast-loading nftables sets and geo-IP lists from IPdeny.
Features:
Fetches US IPv4 + IPv6 ranges (with IPdeny usage-limits respected)
Bulk-loads them efficiently into nftables sets (avoiding slow “one CIDR at a time” loops)
Optional SSH whitelist (IPv4 + IPv6)
Investigation mode that shows:
nftables status
whitelist status
SSH client IP
privileges
missing sets or config issues
Backup + atomic write safety
Nothing applied automatically — you stay in control of `/etc/nftables.conf`
Repo is here:
👉 [https://github.com/baerrs/GeoBlocker](https://github.com/baerrs/GeoBlocker)
# 🛠️ Why I built it
I run a small personal server and kept seeing tons of SSH brute-force attempts from around the world.
Fail2ban helped, but I wanted a stronger approach: just block every non-US address before they even reach SSH.
I found a lot of half-solutions or outdated guides, so I wrote a noscript that:
is reproducible
uses best practices
keeps nftables clean
and is safe for beginners (backups, dry-run behavior, etc.)
# 🙋♂️ What I want feedback on
Since I’m new to publishing open-source noscripts:
Is the structure reasonable?
Any obvious improvements to safety, portability, or code style?
Is the README clear enough?
Any red flags for production usage?
Suggestions for features? (cron auto-update? IPv4/v6 country selection? Better logging?)
I’m totally open to constructive criticism — just keep in mind I’m still learning how to present and share code. ❤️
# Thanks in advance!
If anyone has ideas, corrections, or wants to help evolve the project, I’d really appreciate it.
And if even one person finds it useful, that’s a big win for me already.
Thanks! 🙏
— Scott (R. Scott Baer)
https://redd.it/1p11m9l
@r_bash
GitHub
GitHub - baerrs/GeoBlocker: Geo Blocking
Geo Blocking . Contribute to baerrs/GeoBlocker development by creating an account on GitHub.
Built my own xdg-open alternative because the old one annoyed me — meet YAXO
https://github.com/yogeshdofficial/yaxo
https://redd.it/1p1f8ji
@r_bash
https://github.com/yogeshdofficial/yaxo
https://redd.it/1p1f8ji
@r_bash
GitHub
GitHub - yogeshdofficial/yaxo: Modern replacement for xdg-open
Modern replacement for xdg-open. Contribute to yogeshdofficial/yaxo development by creating an account on GitHub.
i am loosing my mind, help me with bash plz.....
ai: (gpt)
is that a thing really in bash noscripting. bro. i lost hours trying fixing this with gemini cli. finally got this from gpt.
i wrote that line to stop to read "found"
cause my program had tui staff so if i hadn't done that the output would vanish.
bro i am noscripting i have no time for that. after that many days coding with bash... finally this????
idk why but after commenting out the read line it works. how can i avoid unintentional situations like that. this interrupts my flow of work.
https://redd.it/1p1vzik
@r_bash
[[ -f "$dotfiles_path/installer.sh" ]] && echo found
read -n 1 -s -r
if [ -f "$dotfiles_path/installer.sh" ]; then
ai: (gpt)
❗ read -n 1 -s -r breaks the [[ ... ]] test output
read -n 1 reads nothing (because Enter is a newline, not a character key),
leaving the newline in the buffer.
So the NEXT read or the control flow may get triggered early.
This results in:
skipped prompts
next input read incorrectly
if branches executing before expected
depending on where the leftover newline is consumed.
is that a thing really in bash noscripting. bro. i lost hours trying fixing this with gemini cli. finally got this from gpt.
i wrote that line to stop to read "found"
cause my program had tui staff so if i hadn't done that the output would vanish.
bro i am noscripting i have no time for that. after that many days coding with bash... finally this????
idk why but after commenting out the read line it works. how can i avoid unintentional situations like that. this interrupts my flow of work.
https://redd.it/1p1vzik
@r_bash
Reddit
From the bash community on Reddit
Explore this post and more from the bash community
HELP ME
#!/bin/bash
# Decrypt function
function decrypt {
MzSaas7k=$(echo $hash | sed 's/988sn1/83unasa/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/4d298d/9999/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/3i8dqos82/873h4d/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/4n9Ls/20X/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/912oijs01/i7gg/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/k32jx0aa/n391s/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/nI72n/YzF1/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/82ns71n/2d49/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/JGcms1a/zIm12/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/MS9/4SIs/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/Ymxj00Ims/Uso18/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/sSi8Lm/Mit/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/9su2n/43n92ka/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/ggf3iunds/dn3i8/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/uBz/TT0K/g')
flag=$(echo $MzSaas7k | base64 -d | openssl enc -aes-128-cbc -a -d -salt -pass pass:$salt)
}
# Variables
var="9M"
salt=""
hash="VTJGc2RHVmtYMTl2ZnYyNTdUeERVRnBtQWVGNmFWWVUySG1wTXNmRi9rQT0K"
# Base64 Encoding Example:
# $ echo "Some Text" | base64
# <- For-Loop here
# Check if $salt is empty
if [ ! -z "$salt" ]
then
decrypt
echo $flag
else
exit 1
fi
Create a "For" loop that encodes the variable "var" 28 times in "base64". The number of characters in the 28th hash is the value that must be assigned to the "salt" variable.
I have tried every single line of code that i know and still didn't get the right answer
https://redd.it/1p1zx87
@r_bash
#!/bin/bash
# Decrypt function
function decrypt {
MzSaas7k=$(echo $hash | sed 's/988sn1/83unasa/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/4d298d/9999/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/3i8dqos82/873h4d/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/4n9Ls/20X/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/912oijs01/i7gg/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/k32jx0aa/n391s/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/nI72n/YzF1/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/82ns71n/2d49/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/JGcms1a/zIm12/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/MS9/4SIs/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/Ymxj00Ims/Uso18/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/sSi8Lm/Mit/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/9su2n/43n92ka/g')
Mzns7293sk=$(echo $MzSaas7k | sed 's/ggf3iunds/dn3i8/g')
MzSaas7k=$(echo $Mzns7293sk | sed 's/uBz/TT0K/g')
flag=$(echo $MzSaas7k | base64 -d | openssl enc -aes-128-cbc -a -d -salt -pass pass:$salt)
}
# Variables
var="9M"
salt=""
hash="VTJGc2RHVmtYMTl2ZnYyNTdUeERVRnBtQWVGNmFWWVUySG1wTXNmRi9rQT0K"
# Base64 Encoding Example:
# $ echo "Some Text" | base64
# <- For-Loop here
# Check if $salt is empty
if [ ! -z "$salt" ]
then
decrypt
echo $flag
else
exit 1
fi
Create a "For" loop that encodes the variable "var" 28 times in "base64". The number of characters in the 28th hash is the value that must be assigned to the "salt" variable.
I have tried every single line of code that i know and still didn't get the right answer
https://redd.it/1p1zx87
@r_bash
Reddit
From the bash community on Reddit
Explore this post and more from the bash community
Concurrency and Strict Mode
I added a chapter about Bash and Concurrency in my small Bash Strict Mode Guide:
https://github.com/guettli/bash-strict-mode?tab=readme-ov-file#general-bash-hints-concurrency
Feedback is welcome:
## General Bash Hints: Concurrency
If you want to execute two tasks concurrently, you can do it like this:
Why wait each PID separately?
- You must wait to reap background children and avoid zombies.
-
waited for. This means an earlier background job can fail yet the combined
success if the last job succeeds — not what you want if you need to detect failures reliably.
https://redd.it/1p20iz7
@r_bash
I added a chapter about Bash and Concurrency in my small Bash Strict Mode Guide:
https://github.com/guettli/bash-strict-mode?tab=readme-ov-file#general-bash-hints-concurrency
Feedback is welcome:
## General Bash Hints: Concurrency
If you want to execute two tasks concurrently, you can do it like this:
# Bash Strict Mode: https://github.com/guettli/bash-strict-mode
trap 'echo -e "\n🤷 🚨 🔥 Warning: A command has failed. Exiting the noscript. Line was ($0:$LINENO): $(sed -n "${LINENO}p" "$0" 2>/dev/null || true) 🔥 🚨 🤷 "; exit 3' ERR
set -Eeuo pipefail
{
echo task 1
sleep 1
} & task1_pid=$!
{
echo task 2
sleep 2
} & task2_pid=$!
# Wait each PID on its own line so you get each child's exit status.
wait "$task1_pid"
wait "$task2_pid"
echo end
Why wait each PID separately?
- You must wait to reap background children and avoid zombies.
-
wait pid1 pid2 will wait for both PIDs, but its exit status is the exit status of the last PIDwaited for. This means an earlier background job can fail yet the combined
wait can still returnsuccess if the last job succeeds — not what you want if you need to detect failures reliably.
https://redd.it/1p20iz7
@r_bash
GitHub
GitHub - guettli/bash-strict-mode: Bash Strict Mode
Bash Strict Mode. Contribute to guettli/bash-strict-mode development by creating an account on GitHub.
how do you manage your .bashrc and ,bashprofile
Hi
I'm looking at puppet and setting up standard alias and other things
I don't really want to take over \~/.bashrc or \~/.bash\profile
I was thinking maybe the way to do this was to add at the bottom
. (or source) \~/.bashrc-puppet
and
. (or source) \~/.bashrc-local
so that what files or other things can add / remove lines to \~/.bashrc puppet can manage the .bashrc-puppet and local mods can go into .bashrc-local
and the same for the bash_profile
https://redd.it/1p4e3yp
@r_bash
Hi
I'm looking at puppet and setting up standard alias and other things
I don't really want to take over \~/.bashrc or \~/.bash\profile
I was thinking maybe the way to do this was to add at the bottom
. (or source) \~/.bashrc-puppet
and
. (or source) \~/.bashrc-local
so that what files or other things can add / remove lines to \~/.bashrc puppet can manage the .bashrc-puppet and local mods can go into .bashrc-local
and the same for the bash_profile
https://redd.it/1p4e3yp
@r_bash
Reddit
From the bash community on Reddit
Explore this post and more from the bash community
Crypto backup tool
It uses zip and gnupg.
**Features**:
* double encrypt: by zip and by gnupg
* generate hash'es from given password with 1000 iterations, it's prevent easy brute force
* once setup: just use symlinks in backup directory
* ready for cron: just use env variable
* simple for code review and modify
[https://github.com/LazyMiB/Crypto-Backup-Tool](https://github.com/LazyMiB/Crypto-Backup-Tool)
https://redd.it/1p4fjhj
@r_bash
It uses zip and gnupg.
**Features**:
* double encrypt: by zip and by gnupg
* generate hash'es from given password with 1000 iterations, it's prevent easy brute force
* once setup: just use symlinks in backup directory
* ready for cron: just use env variable
* simple for code review and modify
[https://github.com/LazyMiB/Crypto-Backup-Tool](https://github.com/LazyMiB/Crypto-Backup-Tool)
https://redd.it/1p4fjhj
@r_bash
GitHub
GitHub - LazyMiB/Crypto-Backup-Tool: Secure and simple backup tool for GNU/Linux.
Secure and simple backup tool for GNU/Linux. Contribute to LazyMiB/Crypto-Backup-Tool development by creating an account on GitHub.
Beginner-friendly Bash project: Real-time CPU Usage Monitor Script (with alerts + logs)
Sharing a small Bash automation project I built for practice. This noscript monitors CPU usage in real-time using
Step-by-step explanation: https://youtu.be/nVU1JIWGnmI
Complete source code at https://github.com/Abhilashchauhan1994/bash\_noscripts/blob/main/cpu\_usage.sh
https://redd.it/1p4nobz
@r_bash
Sharing a small Bash automation project I built for practice. This noscript monitors CPU usage in real-time using
top \+ awk, sends an alert when the CPU crosses a threshold, and logs usage automatically. Step-by-step explanation: https://youtu.be/nVU1JIWGnmI
Complete source code at https://github.com/Abhilashchauhan1994/bash\_noscripts/blob/main/cpu\_usage.sh
https://redd.it/1p4nobz
@r_bash
YouTube
YOU WON'T BELIEVE How Easy Monitoring CPU Usage Is with Bash
In this step-by-step guide, you’ll learn how to create a CPU Usage Monitor Script using Bash noscripting — one of the most powerful tools for Linux automation.
Whether you’re just starting out or looking to enhance your DevOps and Linux skills, this Bash Scripting…
Whether you’re just starting out or looking to enhance your DevOps and Linux skills, this Bash Scripting…