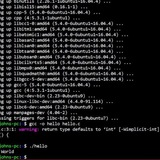
replacement commands:
↳ No builtins are disabled.
======== End of list ========
05:32:47 Tue Dec 02: ~ $ ca -p
╔══════════════════════════════════════════════╗
║ ca – Bash Command Analyzer ║
╚══════════════════════════════════════════════╝
======== PATH Inspection (Mode: -p) ========
├─ Examining PATH directory Order and Permissions:
↳ Directory Perms Owner:Group Note
↳ /home/jb/bin drwxr-xr-x jb:jb Writable
↳ /home/jb/bin/noscripts drwxr-xr-x jb:jb Writable
↳ /home/jb/.local/bin drwxr-xr-x jb:jb Writable
↳ /usr/local/bin drwxr-xr-x root:root
↳ /usr/bin drwxr-xr-x root:root
↳ /bin lrwxrwxrwx root:root
↳ /usr/local/games drwxr-xr-x root:root
↳ /usr/games drwxr-xr-x root:root
======== End of list ========
05:32:53 Tue Dec 02: ~ $ ca -s
╔══════════════════════════════════════════════╗
║ ca – Bash Command Analyzer ║
╚══════════════════════════════════════════════╝
======== Sourced File Inspection (Mode: -s) ========
├─ Searching for files that have been sourced into the enviroment automatically
↳ Discovered the following files:
↳ /home/jb/.bashrc
↳ /usr/share/bash-completion/bash_completion
↳ /etc/bash_completion
↳ /home/jb/.bash_aliases
↳ /home/jb/.bash_functions
↳ /home/jb/.bash_ca
↳ /home/jb/.bash_h
↳ /etc/bash.bashrc
======== End of list ========
05:32:57 Tue Dec 02: ~ $ ca -S
╔══════════════════════════════════════════════╗
║ ca – Bash Command Analyzer ║
╚══════════════════════════════════════════════╝
======== SUID/SGID and World-Writable directories (Mode: -S) ========
├─ Scanning for SUID binaries:
↳ -rwsr-xr-x 1 root root 70888 Apr 19 2025 /usr/bin/chfn
↳ -rwsr-xr-x 1 root root 52936 Apr 19 2025 /usr/bin/chsh
↳ -rwsr-xr-x 1 root root 39224 Jul 16 12:27 /usr/bin/fusermount3
↳ -rwsr-xr-x 1 root root 88568 Apr 19 2025 /usr/bin/gpasswd
↳ -rwsr-xr-x 1 root root 72072 May 9 2025 /usr/bin/mount
↳ -rwsr-xr-x 1 root root 18816 May 9 2025 /usr/bin/newgrp
↳ -rwsr-xr-x 1 root root 166848 Oct 5 2024 /usr/bin/ntfs-3g
↳ -rwsr-xr-x 1 root root 118168 Apr 19 2025 /usr/bin/passwd
↳ -rwsr-xr-x 1 root root 30952 Jan 17 2025 /usr/bin/pkexec
↳ -rwsr-xr-x 1 root root 84360 May 9 2025 /usr/bin/su
↳ -rwsr-xr-x 1 root root 306456 Jun 30 00:55 /usr/bin/sudo
↳ -rwsr-xr-x 1 root root 55688 May 9 2025 /usr/bin/umount
↳ -rwsr-xr-- 1 root messagebus 51272 Mar 8 2025 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
↳ -rwsr-xr-x 1 root root 18512 Apr 18 2025 /usr/libexec/spice-client-glib-usb-acl-helper
↳ -rwsr-xr-x 1 root root 494144 Aug 1 10:02 /usr/lib/openssh/ssh-keysign
↳ -rwsr-xr-x 1 root root 18744 Jan 17 2025 /usr/lib/polkit-1/polkit-agent-helper-1
↳ -rwsr-sr-x 1 root root 14672 Oct 27 12:03 /usr/lib/xorg/Xorg.wrap
↳ -rwsr-xr-x 1 root root 146480 Mar 31 2025 /usr/sbin/mount.nfs
↳ -rwsr-xr-- 1 root dip 428424 Feb 17 2025 /usr/sbin/pppd
├─ Scanning for SGID binaries:
↳ -rwxr-sr-x 1 root shadow 113848 Apr 19 2025 /usr/bin/chage
↳ -rwxr-sr-x 1 root crontab 51936 Jun 13 03:30 /usr/bin/crontab
↳ -rwxr-sr-x 1 root mail 23104 Dec 31 2024 /usr/bin/dotlockfile
↳ -rwxr-sr-x 1 root shadow 31256 Apr 19 2025 /usr/bin/expiry
↳ -rwxr-sr-x 1 root _ssh 420224 Aug 1 10:02 /usr/bin/ssh-agent
↳ -rwxr-sr-x 1 root mail 22784 Nov 5 17:01 /usr/libexec/camel-lock-helper-1.2
↳ -rwxr-sr-x 1
↳ No builtins are disabled.
======== End of list ========
05:32:47 Tue Dec 02: ~ $ ca -p
╔══════════════════════════════════════════════╗
║ ca – Bash Command Analyzer ║
╚══════════════════════════════════════════════╝
======== PATH Inspection (Mode: -p) ========
├─ Examining PATH directory Order and Permissions:
↳ Directory Perms Owner:Group Note
↳ /home/jb/bin drwxr-xr-x jb:jb Writable
↳ /home/jb/bin/noscripts drwxr-xr-x jb:jb Writable
↳ /home/jb/.local/bin drwxr-xr-x jb:jb Writable
↳ /usr/local/bin drwxr-xr-x root:root
↳ /usr/bin drwxr-xr-x root:root
↳ /bin lrwxrwxrwx root:root
↳ /usr/local/games drwxr-xr-x root:root
↳ /usr/games drwxr-xr-x root:root
======== End of list ========
05:32:53 Tue Dec 02: ~ $ ca -s
╔══════════════════════════════════════════════╗
║ ca – Bash Command Analyzer ║
╚══════════════════════════════════════════════╝
======== Sourced File Inspection (Mode: -s) ========
├─ Searching for files that have been sourced into the enviroment automatically
↳ Discovered the following files:
↳ /home/jb/.bashrc
↳ /usr/share/bash-completion/bash_completion
↳ /etc/bash_completion
↳ /home/jb/.bash_aliases
↳ /home/jb/.bash_functions
↳ /home/jb/.bash_ca
↳ /home/jb/.bash_h
↳ /etc/bash.bashrc
======== End of list ========
05:32:57 Tue Dec 02: ~ $ ca -S
╔══════════════════════════════════════════════╗
║ ca – Bash Command Analyzer ║
╚══════════════════════════════════════════════╝
======== SUID/SGID and World-Writable directories (Mode: -S) ========
├─ Scanning for SUID binaries:
↳ -rwsr-xr-x 1 root root 70888 Apr 19 2025 /usr/bin/chfn
↳ -rwsr-xr-x 1 root root 52936 Apr 19 2025 /usr/bin/chsh
↳ -rwsr-xr-x 1 root root 39224 Jul 16 12:27 /usr/bin/fusermount3
↳ -rwsr-xr-x 1 root root 88568 Apr 19 2025 /usr/bin/gpasswd
↳ -rwsr-xr-x 1 root root 72072 May 9 2025 /usr/bin/mount
↳ -rwsr-xr-x 1 root root 18816 May 9 2025 /usr/bin/newgrp
↳ -rwsr-xr-x 1 root root 166848 Oct 5 2024 /usr/bin/ntfs-3g
↳ -rwsr-xr-x 1 root root 118168 Apr 19 2025 /usr/bin/passwd
↳ -rwsr-xr-x 1 root root 30952 Jan 17 2025 /usr/bin/pkexec
↳ -rwsr-xr-x 1 root root 84360 May 9 2025 /usr/bin/su
↳ -rwsr-xr-x 1 root root 306456 Jun 30 00:55 /usr/bin/sudo
↳ -rwsr-xr-x 1 root root 55688 May 9 2025 /usr/bin/umount
↳ -rwsr-xr-- 1 root messagebus 51272 Mar 8 2025 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
↳ -rwsr-xr-x 1 root root 18512 Apr 18 2025 /usr/libexec/spice-client-glib-usb-acl-helper
↳ -rwsr-xr-x 1 root root 494144 Aug 1 10:02 /usr/lib/openssh/ssh-keysign
↳ -rwsr-xr-x 1 root root 18744 Jan 17 2025 /usr/lib/polkit-1/polkit-agent-helper-1
↳ -rwsr-sr-x 1 root root 14672 Oct 27 12:03 /usr/lib/xorg/Xorg.wrap
↳ -rwsr-xr-x 1 root root 146480 Mar 31 2025 /usr/sbin/mount.nfs
↳ -rwsr-xr-- 1 root dip 428424 Feb 17 2025 /usr/sbin/pppd
├─ Scanning for SGID binaries:
↳ -rwxr-sr-x 1 root shadow 113848 Apr 19 2025 /usr/bin/chage
↳ -rwxr-sr-x 1 root crontab 51936 Jun 13 03:30 /usr/bin/crontab
↳ -rwxr-sr-x 1 root mail 23104 Dec 31 2024 /usr/bin/dotlockfile
↳ -rwxr-sr-x 1 root shadow 31256 Apr 19 2025 /usr/bin/expiry
↳ -rwxr-sr-x 1 root _ssh 420224 Aug 1 10:02 /usr/bin/ssh-agent
↳ -rwxr-sr-x 1 root mail 22784 Nov 5 17:01 /usr/libexec/camel-lock-helper-1.2
↳ -rwxr-sr-x 1
root utmp 14416 Nov 12 2024 /usr/lib/x86_64-linux-gnu/utempter/utempter
↳ -rwsr-sr-x 1 root root 14672 Oct 27 12:03 /usr/lib/xorg/Xorg.wrap
↳ -rwxr-sr-x 1 root shadow 43256 Jun 29 12:40 /usr/sbin/unix_chkpwd
├─ Scanning for World-Writable directories:
↳ /run/lock drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /tmp drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /tmp/.font-unix drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /tmp/.XIM-unix drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /tmp/.ICE-unix drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /tmp/.X11-unix drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /dev/mqueue drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /dev/shm drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /var/tmp drwxrwxrwt root:root WORLD-WRITABLE + STICKY
```
---
## Installation
```bash
source /path/to/bash_ca
```
Then call `ca` from your shell.
---
`ca` is useful if you want to:
* Audit your shell for overridden or shadowed commands.
* Inspect binaries for permissions, package info, or SUID/SGID bits.
* Debug complex aliases and shell functions.
* See which files are sourced automatically in your environment.
---
edited to add example
https://redd.it/1pc6f5e
@r_bash
↳ -rwsr-sr-x 1 root root 14672 Oct 27 12:03 /usr/lib/xorg/Xorg.wrap
↳ -rwxr-sr-x 1 root shadow 43256 Jun 29 12:40 /usr/sbin/unix_chkpwd
├─ Scanning for World-Writable directories:
↳ /run/lock drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /tmp drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /tmp/.font-unix drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /tmp/.XIM-unix drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /tmp/.ICE-unix drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /tmp/.X11-unix drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /dev/mqueue drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /dev/shm drwxrwxrwt root:root WORLD-WRITABLE + STICKY
↳ /var/tmp drwxrwxrwt root:root WORLD-WRITABLE + STICKY
```
---
## Installation
```bash
source /path/to/bash_ca
```
Then call `ca` from your shell.
---
`ca` is useful if you want to:
* Audit your shell for overridden or shadowed commands.
* Inspect binaries for permissions, package info, or SUID/SGID bits.
* Debug complex aliases and shell functions.
* See which files are sourced automatically in your environment.
---
edited to add example
https://redd.it/1pc6f5e
@r_bash
Reddit
From the bash community on Reddit: ca – Bash Command Analyzer (aliases, functions, binaries, keywords, noscripts, $PATH & more)
Explore this post and more from the bash community
My bash power toys
I'm happy to bring my own dotfiles to this channel.
https://gitlab.com/hambled/dotfiles
I've been working on it daily for years and have built a lot of tools that I find very useful in my day-to-day work as a sysadmin.
This dotfiles includes interesting tools such as a file explorer (built on fzf), a tool for inspecting commands, variables, and manuals, another for managing various histfiles (contexts) and many more.
The main issue you might have is that it's in Spanish, but it's my native language and the one I feel most comfortable with. I apologize for that "inconvenience."
Bye!
https://redd.it/1pci2vf
@r_bash
I'm happy to bring my own dotfiles to this channel.
https://gitlab.com/hambled/dotfiles
I've been working on it daily for years and have built a lot of tools that I find very useful in my day-to-day work as a sysadmin.
This dotfiles includes interesting tools such as a file explorer (built on fzf), a tool for inspecting commands, variables, and manuals, another for managing various histfiles (contexts) and many more.
The main issue you might have is that it's in Spanish, but it's my native language and the one I feel most comfortable with. I apologize for that "inconvenience."
Bye!
https://redd.it/1pci2vf
@r_bash
GitLab
Alberto Millán / dotfiles · GitLab
Ficheros de configuración
Tmux not starting from noscript
\#!/bin/bash
\#python study workspace
hyprctl dispatch workspace 1
hyprctl dispatch exec "kitty -e sh -lc '/usr/bin/tmux a -t cs50p || /usr/bin/tmux exec bash'"
sleep 2
hyprctl dispatch exec brave "https://www.youtube.com/playlist?list=PLhQjrBD2T3817j24-GogXmWqO5Q5vYy0V \\
https://cs50.harvard.edu/python/psets/6/ \\
https://github.com/cyberseekerx"
sleep 3
hyprctl dispatch workspace 10
hyprctl dispatch exec kitty "\~/Videos/"
\## the problem here is that when I try to use this noscript fresh start (as in after booting)
\#but works after starting tmux instance other things work
thanks for you'r help in advance
https://redd.it/1pcwa64
@r_bash
\#!/bin/bash
\#python study workspace
hyprctl dispatch workspace 1
hyprctl dispatch exec "kitty -e sh -lc '/usr/bin/tmux a -t cs50p || /usr/bin/tmux exec bash'"
sleep 2
hyprctl dispatch exec brave "https://www.youtube.com/playlist?list=PLhQjrBD2T3817j24-GogXmWqO5Q5vYy0V \\
https://cs50.harvard.edu/python/psets/6/ \\
https://github.com/cyberseekerx"
sleep 3
hyprctl dispatch workspace 10
hyprctl dispatch exec kitty "\~/Videos/"
\## the problem here is that when I try to use this noscript fresh start (as in after booting)
\#but works after starting tmux instance other things work
thanks for you'r help in advance
https://redd.it/1pcwa64
@r_bash
YouTube
CS50's Introduction to Programming with Python (CS50P) 2022
This is CS50P, CS50's Introduction to Programming with Python. Register for free at https://cs50.edx.org/python. Slides and source code at https://cs50.harva...
I wrote a Bash wrapper for Nmap & Gobuster with HTML reporting (AlienTec Recon V2.0)
Hi r/bash,
I've been working on a project to practice my noscripting skills and automate my daily pentesting workflow. I just released Version 2.0 and would love some feedback on the code and logic.
What is it?
It's a native Bash noscript that orchestrates Nmap (Port scanning) and Gobuster (Directory forcing) into a single flow. It parses the output and generates a clean HTML report at the end.
The Script Features:
🐧 Pure Bash: Runs natively on Linux (Kali/Parrot) without Python dependencies.
🚀 Orchestration: Handles background processes for scanning.
📄 Reporting: Uses `cat` and heredocs to generate a styled HTML report.
🔍 Logic: Automatically detects if the target is internal or external to adjust scan intensity.
Repository:
https://github.com/AlienTec1908/AlienTec-Recon-Tool
I'm open to code reviews! If you see any bad practices or ways to optimize the loops/arrays, let me know.
Thanks!
https://redd.it/1pecxw3
@r_bash
Hi r/bash,
I've been working on a project to practice my noscripting skills and automate my daily pentesting workflow. I just released Version 2.0 and would love some feedback on the code and logic.
What is it?
It's a native Bash noscript that orchestrates Nmap (Port scanning) and Gobuster (Directory forcing) into a single flow. It parses the output and generates a clean HTML report at the end.
The Script Features:
🐧 Pure Bash: Runs natively on Linux (Kali/Parrot) without Python dependencies.
🚀 Orchestration: Handles background processes for scanning.
📄 Reporting: Uses `cat` and heredocs to generate a styled HTML report.
🔍 Logic: Automatically detects if the target is internal or external to adjust scan intensity.
Repository:
https://github.com/AlienTec1908/AlienTec-Recon-Tool
I'm open to code reviews! If you see any bad practices or ways to optimize the loops/arrays, let me know.
Thanks!
https://redd.it/1pecxw3
@r_bash
GitHub
GitHub - AlienTec1908/AlienTec-Recon-Tool: AlienTec-Recon-Tool
AlienTec-Recon-Tool. Contribute to AlienTec1908/AlienTec-Recon-Tool development by creating an account on GitHub.
Llib - I created a Bash library with argument parsing, finally and much more
I’ve been playing with Bash for a few years now. Every time I ran into something that I feel is missing, I try to hack together a solution. After enough time this turned into a whole library: [https://kamilcuk.github.io/L\lib/](https://kamilcuk.github.io/Llib/) . Few modules changed how I write Bash.
[L\argparse](https://kamilcuk.github.io/Llib/section/argparse/) has argument parsing with interface like Pythons argparse. I never liked existing argument parsing libraries in Bash, so I wrote my own (yay!). It generates helps, has shell completion, colors, subparsers, function subparsers and more.
[L\finally](https://kamilcuk.github.io/Llib/section/finally/) allows to register a cleanup function that is always run on noscript exit. Or on the current function return, whichever comes first. Functions can nested, each function call has own cleanups. Finally a useful use of the RETURN trap, that trap is shared between all Bash functions. This ended up being more useful then I expected.
[L\setx](https://kamilcuk.github.io/Llib/section/stdlib/?h=lsetx#Llib.sh--Lsetx) just enables
L\_print\_traceback prints the traceback similar to Python. I found this post ages ago. I like using
The project grew far larger than I intended, partly as my like research project if it is possible to implement Bash standard library. I doubt it is finished. There are probably many more bugs. Either way, I use parts of the library daily within my noscripts.
Full source: https://github.com/kamilcuk/L\_lib/ . That's all, live long and have fun.
https://redd.it/1pfmzot
@r_bash
I’ve been playing with Bash for a few years now. Every time I ran into something that I feel is missing, I try to hack together a solution. After enough time this turned into a whole library: [https://kamilcuk.github.io/L\lib/](https://kamilcuk.github.io/Llib/) . Few modules changed how I write Bash.
[L\argparse](https://kamilcuk.github.io/Llib/section/argparse/) has argument parsing with interface like Pythons argparse. I never liked existing argument parsing libraries in Bash, so I wrote my own (yay!). It generates helps, has shell completion, colors, subparsers, function subparsers and more.
[L\finally](https://kamilcuk.github.io/Llib/section/finally/) allows to register a cleanup function that is always run on noscript exit. Or on the current function return, whichever comes first. Functions can nested, each function call has own cleanups. Finally a useful use of the RETURN trap, that trap is shared between all Bash functions. This ended up being more useful then I expected.
[L\setx](https://kamilcuk.github.io/Llib/section/stdlib/?h=lsetx#Llib.sh--Lsetx) just enables
set -x for one command and then unsets it. Stupidly simple, insanely useful, I am surprised how often I slap "L_setx", because it unsets -x automatically, making the output clearer. There is also L_unsetx.L\_print\_traceback prints the traceback similar to Python. I found this post ages ago. I like using
set -e and trap ERR and printing traceback on error. Plus helpers like L\_assert L\_panic very simple function, I think everyone implements something like this.The project grew far larger than I intended, partly as my like research project if it is possible to implement Bash standard library. I doubt it is finished. There are probably many more bugs. Either way, I use parts of the library daily within my noscripts.
Full source: https://github.com/kamilcuk/L\_lib/ . That's all, live long and have fun.
https://redd.it/1pfmzot
@r_bash
Help
Hello!
I am a young developer from India , developing for a startup , can anybody tell me how may I customize whole linux gui with my own writen HTML , CSS and JS code, how to connect them with my backend, I want to run my own gui in top of gnome of linux mint , please help me. I don't have a lot of experience but a very curious and creative mind..plz help
https://redd.it/1pft0zq
@r_bash
Hello!
I am a young developer from India , developing for a startup , can anybody tell me how may I customize whole linux gui with my own writen HTML , CSS and JS code, how to connect them with my backend, I want to run my own gui in top of gnome of linux mint , please help me. I don't have a lot of experience but a very curious and creative mind..plz help
https://redd.it/1pft0zq
@r_bash
Reddit
From the bash community on Reddit
Explore this post and more from the bash community
throt: bash utility for delay a cli command and run it only once
https://github.com/hmepas/throt
Mac OS X installation thru brew:
brew tap hmepas/homebrew-throt
brew install throt
Or just download
curl -o ~/bin/throt https://raw.githubusercontent.com/hmepas/throt/refs/heads/main/throt && chmod +x ~/bin/throt
(or whatever)
Usage example:
throt --delay 5 yabairearrangespaces.sh
What's the idea. I.e. I have a yabai trigger for changing display layout (adding 2nd monitor or removing it) the problem is this trigger is noisy for comming out of sleep it could be fired several times, first for removing monitor and second for adding it back again when OS recognize it's have one. Also I do not need to run my rearrange displays noscript imideately, since I need to give system itself time to react and yabai time to adjust first. Also there is no reason to run this rearranging twice, first there are possibly be race condition and secondly it's just don't neccessary. So i wrote a simple bash noscript which on the first run create a lock file and detached proccess with sleep <sec> inside. After sleep is done the command is fired. And all calls before that will be just dissmissed for that particular command.
Enjoy!
https://redd.it/1pfn0si
@r_bash
https://github.com/hmepas/throt
Mac OS X installation thru brew:
brew tap hmepas/homebrew-throt
brew install throt
Or just download
curl -o ~/bin/throt https://raw.githubusercontent.com/hmepas/throt/refs/heads/main/throt && chmod +x ~/bin/throt
(or whatever)
Usage example:
throt --delay 5 yabairearrangespaces.sh
What's the idea. I.e. I have a yabai trigger for changing display layout (adding 2nd monitor or removing it) the problem is this trigger is noisy for comming out of sleep it could be fired several times, first for removing monitor and second for adding it back again when OS recognize it's have one. Also I do not need to run my rearrange displays noscript imideately, since I need to give system itself time to react and yabai time to adjust first. Also there is no reason to run this rearranging twice, first there are possibly be race condition and secondly it's just don't neccessary. So i wrote a simple bash noscript which on the first run create a lock file and detached proccess with sleep <sec> inside. After sleep is done the command is fired. And all calls before that will be just dissmissed for that particular command.
Enjoy!
https://redd.it/1pfn0si
@r_bash
GitHub
GitHub - hmepas/throt
Contribute to hmepas/throt development by creating an account on GitHub.
Get filename expansion to work with “here strings”?
Unless -f is specified, bash expands filenames as stated here:
But I was pretty surprised that this one didn’t work as expected:
In this page about here strings it’s clearly written:
> Filename expansion and word splitting are not performed.
There is no information on how to get filename expansions to work with this syntax. Shell flags? Patches? Workarounds? Any particular reason why it does variable expansion in here strings, but not filename one?
Thanks!
https://redd.it/1ph92p9
@r_bash
Unless -f is specified, bash expands filenames as stated here:
% echo /var/cache/*
/var/cache/apk /var/cache/misc
But I was pretty surprised that this one didn’t work as expected:
cat <<< /var/cache/*
/var/cache/*
In this page about here strings it’s clearly written:
> Filename expansion and word splitting are not performed.
There is no information on how to get filename expansions to work with this syntax. Shell flags? Patches? Workarounds? Any particular reason why it does variable expansion in here strings, but not filename one?
Thanks!
https://redd.it/1ph92p9
@r_bash
www.gnu.org
Bash Features ¶
Next: Introduction, Previous: (dir), Up: (dir) [Contents][Index]
I made this Bash keyboard shortcuts map because I was tired of forgetting them 😅
Hey everyone!
I’ve always seen visual “keyboard maps” for apps like GIMP, Photoshop, Blender,
etc. — where each key is labeled with its shortcut. But I realized I had never
seen a version of that style specifically for Bash / Readline shortcuts.
So I decided to design one.
Part of the inspiration came from the classic Vi/Vim cheat sheet from ViEmu:
http://www.viemu.com/a\_vi\_vim\_graphical\_cheat\_sheet\_tutorial.html
What I really liked was how it uses the keyboard itself as the visual foundation,
and how the shortcuts are introduced progressively rather than all at once.
I wanted to recreate that idea for Bash/Readline, since most Bash shortcut
references are just plain text lists.
Following that concept, I made **four versions** of the Bash shortcuts map,
ranging from a very basic level to more advanced ones, so learners can progress
naturally as they get more comfortable with Readline.
Here’s the image:
Bash cheatsheet full version
The full set of versions is available here:
https://github.com/Athesto/cheatsheets
Features:
• Cursor and word movement
• Reverse/forward history search
• Kill/yank/transpose editing commands
• Ctrl, Meta (Alt/Opt), and Shift combos
• Color-coded categories
• Based on Readline defaults
• 4 progressive levels available in the repo
License (CC BY-SA 4.0):
You’re free to use, share, remix, or include this in teaching materials
(including commercial ones) as long as proper credit is given and derivative
works are shared under the same license. I wanted people to reuse it without
worrying about permissions.
Hope this helps anyone learning or teaching Bash!
Feedback and suggestions are very welcome.
https://redd.it/1phy40k
@r_bash
Hey everyone!
I’ve always seen visual “keyboard maps” for apps like GIMP, Photoshop, Blender,
etc. — where each key is labeled with its shortcut. But I realized I had never
seen a version of that style specifically for Bash / Readline shortcuts.
So I decided to design one.
Part of the inspiration came from the classic Vi/Vim cheat sheet from ViEmu:
http://www.viemu.com/a\_vi\_vim\_graphical\_cheat\_sheet\_tutorial.html
What I really liked was how it uses the keyboard itself as the visual foundation,
and how the shortcuts are introduced progressively rather than all at once.
I wanted to recreate that idea for Bash/Readline, since most Bash shortcut
references are just plain text lists.
Following that concept, I made **four versions** of the Bash shortcuts map,
ranging from a very basic level to more advanced ones, so learners can progress
naturally as they get more comfortable with Readline.
Here’s the image:
Bash cheatsheet full version
The full set of versions is available here:
https://github.com/Athesto/cheatsheets
Features:
• Cursor and word movement
• Reverse/forward history search
• Kill/yank/transpose editing commands
• Ctrl, Meta (Alt/Opt), and Shift combos
• Color-coded categories
• Based on Readline defaults
• 4 progressive levels available in the repo
License (CC BY-SA 4.0):
You’re free to use, share, remix, or include this in teaching materials
(including commercial ones) as long as proper credit is given and derivative
works are shared under the same license. I wanted people to reuse it without
worrying about permissions.
Hope this helps anyone learning or teaching Bash!
Feedback and suggestions are very welcome.
https://redd.it/1phy40k
@r_bash
Help me on good shebang practice !!
as i knew that its a good practice to add shebang in the starting of noscript, i used it in all my projects. `#!/bin/bash` used it in my linutils and other repositories that depend on bash.
but now i started using NixOS and it shows bad interprator or something like that(an error).
i found about `#/usr/bin/env bash`
should i use it in all my repositories that need to run on debian/arch/fedora. i mean "is this shebang universally acceptable"
https://redd.it/1pi50s9
@r_bash
as i knew that its a good practice to add shebang in the starting of noscript, i used it in all my projects. `#!/bin/bash` used it in my linutils and other repositories that depend on bash.
but now i started using NixOS and it shows bad interprator or something like that(an error).
i found about `#/usr/bin/env bash`
should i use it in all my repositories that need to run on debian/arch/fedora. i mean "is this shebang universally acceptable"
https://redd.it/1pi50s9
@r_bash
Reddit
From the bash community on Reddit
Explore this post and more from the bash community
bash bash bash
idk pero hindi talaga ako nagagandahan don sa fAt!m@ A. na content creator galing sa tiktok 😭 ang oa niy for me. naiinis ako sa pag,umukha niya. ako lang ba like they aint cute bro they look like baliw
https://redd.it/1pi69xh
@r_bash
idk pero hindi talaga ako nagagandahan don sa fAt!m@ A. na content creator galing sa tiktok 😭 ang oa niy for me. naiinis ako sa pag,umukha niya. ako lang ba like they aint cute bro they look like baliw
https://redd.it/1pi69xh
@r_bash
Reddit
From the bash community on Reddit
Explore this post and more from the bash community
New or Old Bash guide
I see the bash tutorial in the side bar has a new version but the sub lists the old one. Which is recommended?
https://redd.it/1piqz4y
@r_bash
I see the bash tutorial in the side bar has a new version but the sub lists the old one. Which is recommended?
https://redd.it/1piqz4y
@r_bash
Reddit
From the bash community on Reddit
Explore this post and more from the bash community
Why doesnt this command work on a mac?
https://redd.it/1pivezi
@r_bash
Input
echo "Udemy - The AI Engineer Course 2025 Complete AI Engineer Bootcamp (8.2025)" | sed -E 's/\s+/-/g'
Output
Udemy - The AI Engineer Cour-e 2025 Complete AI Engineer Bootcamp (8.2025)
https://redd.it/1pivezi
@r_bash
Reddit
From the bash community on Reddit
Explore this post and more from the bash community
I'm attempting to mimic multi-dimensional arrays for a personal use noscript. What I am currently doing is wrong and I can't seem to find a way to do it correctly.
\#List_out is an output of a func that generates surnames, traits and other information
\#List_out is currently a generated Surname
surnames+=("$List_out") #list of every surname
declare -a $List_out #list of connected items to the surname
\#List_out is now a first name connected to the most recently generated surname
eval "${surnames[-1\]}+=("$List_out")"
declare -A $List_out #name of individual (store characteristics)
\#List_out is now a chosen string and quirks is supposed to be the key for the associative array that was just defined
\#the second -1 refers to the last generated name in the array
eval "${{surnames[-1\]}[-1\]}[Quirks\]=$List_out"
If anyone has any suggestions I would be very grateful.
https://redd.it/1pjat85
@r_bash
\#List_out is an output of a func that generates surnames, traits and other information
\#List_out is currently a generated Surname
surnames+=("$List_out") #list of every surname
declare -a $List_out #list of connected items to the surname
\#List_out is now a first name connected to the most recently generated surname
eval "${surnames[-1\]}+=("$List_out")"
declare -A $List_out #name of individual (store characteristics)
\#List_out is now a chosen string and quirks is supposed to be the key for the associative array that was just defined
\#the second -1 refers to the last generated name in the array
eval "${{surnames[-1\]}[-1\]}[Quirks\]=$List_out"
If anyone has any suggestions I would be very grateful.
https://redd.it/1pjat85
@r_bash
Reddit
From the bash community on Reddit
Explore this post and more from the bash community
noob Can simple noscript with mapfile be improved?
I have this simple noscript that finds empty directories recursively, opens a list of them with vim for user to edit (delete lines to omit from removal), then on save and exit, prints the updated list to prompt for removal.
Can the noscript be simplified? Open to all constructive criticism, however minor and nitpick, as well as personal preferences from experienced bash users.
Note:
https://redd.it/1pjmqff
@r_bash
I have this simple noscript that finds empty directories recursively, opens a list of them with vim for user to edit (delete lines to omit from removal), then on save and exit, prints the updated list to prompt for removal.
Can the noscript be simplified? Open to all constructive criticism, however minor and nitpick, as well as personal preferences from experienced bash users.
Note:
fd is not as standard as find command and I don't see the point of avoiding bashisms in the noscript since arrays were used anyway.https://redd.it/1pjmqff
@r_bash
Avoiding Multiprocessing Errors in Bash Shell
https://www.johndcook.com/blog/2024/02/12/avoiding-multiprocessing-errors-in-bash-shell/
https://redd.it/1pkj7x8
@r_bash
https://www.johndcook.com/blog/2024/02/12/avoiding-multiprocessing-errors-in-bash-shell/
https://redd.it/1pkj7x8
@r_bash
John D. Cook | Applied Mathematics Consulting
Multiprocess Errors | Bash Shell | Linux | Multithreading
Errors are easy to make when programming multiple concurrent processes or threads. Using atomic operations and well-formed locks can help to avoid such errors.