Why does this loop exit early?
I have a text file containing a list of file names, one per line, that I want to download from a remote host (a seedbox hosted with feralhosting). The text file contains only partial file names, so I need to find the file on the remote host first. e.g., the text file might have "Miami Connection" and on the remote host it's "Miami Connection (1987).mkv".
Initially I was just doing this:
This would download 1 - 3 files then exit (rather than iterate over the full text file as I expected). I'd delete the lines that were downloaded from the list and restart. It would grab a few more files then exit again... The downloads always complete and it would exit after a very random amount of execution time. Nothing appears to be killing it. The job always exits as if it reached the end of the file, but it should be reading more lines.
I'm trying to figure out why it's exiting. I've expanded it into a small noscript with some diagnostic output and have gotten it down to this (no file transfer so it runs very quickly):
#!/bin/bash
set -x
while read i ; do
unset f
echo "==$i=="
f=$(ssh myhost "ls ~/files/ | grep \"$i\"" | head -1)
if [ $f ] ; then
echo "found $f"
else
echo "couldn't find $i"
fi
done <test
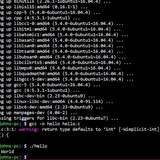
If I comment out the ssh line, it'll iterate over the entire file. If I leave the ssh line, it always stops early. To rule out any weirdness in the text file, I created a new one, making sure it's just plain text:
With the test file it always stops after the first line. The "mkv" line is the only one that should match anything on the remote host. It doesn't matter where I put that in the text file -- the noscript always stops after line one. Again if I comment out the ssh line, it goes through the whole text file. The output is like:
+ read i
+ unset f
+ echo '==not a file=='
==not a file==
++ ssh myhost 'ls ~/files/ | grep "not a file" | head -1'
+ f=
+ [ -n '' ]
+ echo 'couldn'\''t find not a file'
couldn't find not a file
+ read i
Can anyone explain what I'm doing wrong here/why it won't read the entire file? I'm not really looking for better/alternate ways of doing this. Just trying to understand what's happening here.
https://redd.it/11p4cbr
@r_bash
I have a text file containing a list of file names, one per line, that I want to download from a remote host (a seedbox hosted with feralhosting). The text file contains only partial file names, so I need to find the file on the remote host first. e.g., the text file might have "Miami Connection" and on the remote host it's "Miami Connection (1987).mkv".
Initially I was just doing this:
while read i ; do f=$(ssh myhost "ls -1 ~/files/ | grep \"$i\"") ; scp myhost:~/files/"$f" . ; done <file_listThis would download 1 - 3 files then exit (rather than iterate over the full text file as I expected). I'd delete the lines that were downloaded from the list and restart. It would grab a few more files then exit again... The downloads always complete and it would exit after a very random amount of execution time. Nothing appears to be killing it. The job always exits as if it reached the end of the file, but it should be reading more lines.
I'm trying to figure out why it's exiting. I've expanded it into a small noscript with some diagnostic output and have gotten it down to this (no file transfer so it runs very quickly):
#!/bin/bash
set -x
while read i ; do
unset f
echo "==$i=="
f=$(ssh myhost "ls ~/files/ | grep \"$i\"" | head -1)
if [ $f ] ; then
echo "found $f"
else
echo "couldn't find $i"
fi
done <test
If I comment out the ssh line, it'll iterate over the entire file. If I leave the ssh line, it always stops early. To rule out any weirdness in the text file, I created a new one, making sure it's just plain text:
printf "not a file\nmkv\nalso not a file\nnoperino" > testWith the test file it always stops after the first line. The "mkv" line is the only one that should match anything on the remote host. It doesn't matter where I put that in the text file -- the noscript always stops after line one. Again if I comment out the ssh line, it goes through the whole text file. The output is like:
+ read i
+ unset f
+ echo '==not a file=='
==not a file==
++ ssh myhost 'ls ~/files/ | grep "not a file" | head -1'
+ f=
+ [ -n '' ]
+ echo 'couldn'\''t find not a file'
couldn't find not a file
+ read i
Can anyone explain what I'm doing wrong here/why it won't read the entire file? I'm not really looking for better/alternate ways of doing this. Just trying to understand what's happening here.
https://redd.it/11p4cbr
@r_bash
Reddit
r/bash on Reddit: Why does this loop exit early?
Posted by u/KangarooDouble7454 - No votes and 1 comment
bash-annotations: A bash framework for creating custom injection and function hook style annotations
Source code: https://github.com/david-luison-starkey/bash-annotations
Showcase project: https://github.com/david-luison-starkey/bash-annotations-toolbox
https://redd.it/11p6cs4
@r_bash
Source code: https://github.com/david-luison-starkey/bash-annotations
Showcase project: https://github.com/david-luison-starkey/bash-annotations-toolbox
https://redd.it/11p6cs4
@r_bash
GitHub
GitHub - david-luison-starkey/bash-annotations: Java-style annotations for Bash
Java-style annotations for Bash. Contribute to david-luison-starkey/bash-annotations development by creating an account on GitHub.
Command works on Linux Mint terminal, but my sytax are wrong to work under Linux Mint in a starter.
The follow one works on terminal:
gsettings reset org.x.editor.state.history-entry history-replace-with
​
I tryed the follow one on on terminal, later I will use it on starter, but got the follow error message:
bash -c 'gsettings reset org.x.editor.state.history-entry history-replace-with; -c'
bash: -c: Command not found.
​
Any idea?
https://redd.it/11pjnew
@r_bash
The follow one works on terminal:
gsettings reset org.x.editor.state.history-entry history-replace-with
​
I tryed the follow one on on terminal, later I will use it on starter, but got the follow error message:
bash -c 'gsettings reset org.x.editor.state.history-entry history-replace-with; -c'
bash: -c: Command not found.
​
Any idea?
https://redd.it/11pjnew
@r_bash
Reddit
r/bash on Reddit: Command works on Linux Mint terminal, but my sytax are wrong to work under Linux Mint in a starter.
Posted by u/TitleApprehensive360 - No votes and no comments
Is there a better way to remove all files of certain extension except most recent?
Multiple backups are created within and named something like;
I'm needing a way to delete
The below works only if there aren't any spaces in the filenames. Sadly, sometimes there are indeed spaces in the filename.
#!/bin/bash
# ~/.noscripts/mynoscript.sh
# Gets run daily via systemd service and timer
myDir="$HOME/Documents/Blah/Foo Bar~D45EAG74.foo/"
myCount=$(find ~/Documents/Blah/Foo Bar~D45EAG74.foo"/ -type f -name '.backup' | wc -l)
if [ "$myCount" -ge 2 ]; then
cd "$myDir"
ls .backup | head -n -1 | xargs rm --
cd --
fi
I'm hoping there's a cleaner/more efficient way to do this while fixing it so spaces aren't an problem anymore. You can also see that one line has
Can anyone help me find some solutions?
https://redd.it/11ptomy
@r_bash
~/Documents/Blah/Foo Bar~D45EAG74.foo/ contains a bunch of files and folders. Multiple backups are created within and named something like;
Backup_2023-03-12T18-13-02_A_028E165A-42CB-E084-F0C8-04C8EE231D82.backupI'm needing a way to delete
*.backup files while leaving the most recent one alone.The below works only if there aren't any spaces in the filenames. Sadly, sometimes there are indeed spaces in the filename.
#!/bin/bash
# ~/.noscripts/mynoscript.sh
# Gets run daily via systemd service and timer
myDir="$HOME/Documents/Blah/Foo Bar~D45EAG74.foo/"
myCount=$(find ~/Documents/Blah/Foo Bar~D45EAG74.foo"/ -type f -name '.backup' | wc -l)
if [ "$myCount" -ge 2 ]; then
cd "$myDir"
ls .backup | head -n -1 | xargs rm --
cd --
fi
I'm hoping there's a cleaner/more efficient way to do this while fixing it so spaces aren't an problem anymore. You can also see that one line has
$HOME and another has a ~ in their paths. This triggers my OCD but I'm not sure how to fix it. Can anyone help me find some solutions?
https://redd.it/11ptomy
@r_bash
Trying to Grep urls
I am trying to find a way to find urls (specifically jpgs) with grep, but I just cant seem to find the secret sauce to get the command to work.
what I have right now is
grep -o http.*.jpg jpgfiles.txt
https://redd.it/11pvnjk
@r_bash
I am trying to find a way to find urls (specifically jpgs) with grep, but I just cant seem to find the secret sauce to get the command to work.
what I have right now is
grep -o http.*.jpg jpgfiles.txt
https://redd.it/11pvnjk
@r_bash
Reddit
r/bash on Reddit: Trying to Grep urls
Posted by u/Rogue_Intelligence - No votes and 1 comment
I made a repo for useful bash noscripts
https://github.com/wolandark/BASH\_Scripts\_For\_Everyone
These are my personal bash noscripts that I thought other people might also find useful. I'm hoping that other people cleverer than I will contribute to the repo and make it a large bank of shell noscripts in one place. I will continue to push more noscripts if I come up with anything new and handy. I'll gladly accept PRs and ideas and suggestions.
cheers!
https://redd.it/11pyc2l
@r_bash
https://github.com/wolandark/BASH\_Scripts\_For\_Everyone
These are my personal bash noscripts that I thought other people might also find useful. I'm hoping that other people cleverer than I will contribute to the repo and make it a large bank of shell noscripts in one place. I will continue to push more noscripts if I come up with anything new and handy. I'll gladly accept PRs and ideas and suggestions.
cheers!
https://redd.it/11pyc2l
@r_bash
GitHub
GitHub - wolandark/BASH_Scripts_For_Everyone: A collection of BASH noscripts that might benefit all *nix users
A collection of BASH noscripts that might benefit all *nix users - wolandark/BASH_Scripts_For_Everyone
How to compare 2 strings and store output to variable without if statement?
Basically I want to achieve something like this
compare="str1" == "str2"
where
https://redd.it/11pxlzf
@r_bash
Basically I want to achieve something like this
compare="str1" == "str2"
where
$compare would either TRUE of FALSEhttps://redd.it/11pxlzf
@r_bash
Reddit
r/bash on Reddit: How to compare 2 strings and store output to variable without if statement?
Posted by u/Dragonaax - No votes and 6 comments
Is this the correct way of setting environmental variables in bash ?
I have these environmental variables in csh
setenv CDS_ENABLE_EXP_PCELL true
setenv CDS_EXP_PCELL_DIR ./.expressPcells
If I were to set the same variables in Bash will this be the correct format:
export CDS_ENABLE_EXP_PCELL=true
export CDS_EXP_PCELL_DIR=$CDS_EXP_PCELL_DIR: ./.expressPcells
https://redd.it/11qcsvk
@r_bash
I have these environmental variables in csh
setenv CDS_ENABLE_EXP_PCELL true
setenv CDS_EXP_PCELL_DIR ./.expressPcells
If I were to set the same variables in Bash will this be the correct format:
export CDS_ENABLE_EXP_PCELL=true
export CDS_EXP_PCELL_DIR=$CDS_EXP_PCELL_DIR: ./.expressPcells
https://redd.it/11qcsvk
@r_bash
Reddit
r/bash on Reddit: Is this the correct way of setting environmental variables in bash ?
Posted by u/error_5050 - No votes and no comments
[help] Given the output of "df -h"... how to...
Given the output of the "df -h", how to find out the corresponding disk device with single command ? All I am trying to list out the corresponding block device that "/dev/mapper/vg\_name-lvol0" is mounted on. Cheers !
[root@my-host]# df -h
Filesystem Size Used Avail Use% Mounted on
devtmpfs 7.7G 0 7.7G 0% /dev
tmpfs 7.7G 0 7.7G 0% /dev/shm
tmpfs 7.7G 25M 7.7G 1% /run
tmpfs 7.7G 0 7.7G 0% /sys/fs/cgroup
/dev/nvme0n1p2 20G 4.5G 16G 23% /
tmpfs 1.6G 0 1.6G 0% /run/user/1000
/dev/mapper/vg_name-lvol0 1016M 740M 277M 73% /hellworld
https://redd.it/11qfai7
@r_bash
Given the output of the "df -h", how to find out the corresponding disk device with single command ? All I am trying to list out the corresponding block device that "/dev/mapper/vg\_name-lvol0" is mounted on. Cheers !
[root@my-host]# df -h
Filesystem Size Used Avail Use% Mounted on
devtmpfs 7.7G 0 7.7G 0% /dev
tmpfs 7.7G 0 7.7G 0% /dev/shm
tmpfs 7.7G 25M 7.7G 1% /run
tmpfs 7.7G 0 7.7G 0% /sys/fs/cgroup
/dev/nvme0n1p2 20G 4.5G 16G 23% /
tmpfs 1.6G 0 1.6G 0% /run/user/1000
/dev/mapper/vg_name-lvol0 1016M 740M 277M 73% /hellworld
https://redd.it/11qfai7
@r_bash
Reddit
r/bash on Reddit: [help] Given the output of "df -h"... how to...
Posted by u/BlueAcronis - No votes and no comments
Copy files based on txt file
I must be doing something wrong here while I’m trying bash to copy (with overwrite option) all the files based on txt files, which contains source and destination paths, multiple, different paths.
I tried with cat, with xargs, with no avail…
Any suggestions will be much appreciated.
TiA
https://redd.it/11qg9kd
@r_bash
I must be doing something wrong here while I’m trying bash to copy (with overwrite option) all the files based on txt files, which contains source and destination paths, multiple, different paths.
I tried with cat, with xargs, with no avail…
Any suggestions will be much appreciated.
TiA
https://redd.it/11qg9kd
@r_bash
Reddit
r/bash on Reddit: Copy files based on txt file
Posted by u/xattrX - No votes and no comments
Cannot match character limit with regex
I have a bit of regex I'm struggling with and cannot seem to get it to only allow up to 20 characters.
I want it to match either with max of 20 characters in length:
I do not want it to match:
This is what I have:
What's wrong with this?
https://redd.it/11qihgm
@r_bash
I have a bit of regex I'm struggling with and cannot seem to get it to only allow up to 20 characters.
I want it to match either with max of 20 characters in length:
test test-123 I do not want it to match:
test- -test test-123- This is what I have:
^([A-Za-z0-9]+)([-A-Za-z0-9]*)([A-Za-z0-9]+).{1,20}$'What's wrong with this?
https://redd.it/11qihgm
@r_bash
Reddit
r/bash on Reddit: Cannot match character limit with regex
Posted by u/bluegreen456 - No votes and no comments
bash noscript to send disk usage telegram alert
Hello, I have found this interesting noscript googling but it gives me error on line 12 ans 18 percent not found and let not found. Can someone help me fixing it ?
#!/bin/bash
USERID="XXX" #Chat to u/getidbot
KEY="XXX" #Telegram Secret Code
URL="https://api.telegram.org/bot$KEY/sendMessage"
TIMEOUT="10"
threshold="90" #Set Custom Threshold
i=2
result=
for percent in $result; do
if ((percent > threshold))
then
partition=
TEXT="$partition at $(hostname -f) is ${percent}% full"
curl -s --max-time $TIMEOUT -d "chatid=$USERID&disablewebpagepreview=1&text=$TEXT" $URL > /dev/null
fi
let i=$i+1
done
https://redd.it/11qirwo
@r_bash
Hello, I have found this interesting noscript googling but it gives me error on line 12 ans 18 percent not found and let not found. Can someone help me fixing it ?
#!/bin/bash
USERID="XXX" #Chat to u/getidbot
KEY="XXX" #Telegram Secret Code
URL="https://api.telegram.org/bot$KEY/sendMessage"
TIMEOUT="10"
threshold="90" #Set Custom Threshold
i=2
result=
df -kh /dev/sda1 |grep -v "Filesystem" | awk '{ print $5 }' | sed 's/%//g' for percent in $result; do
if ((percent > threshold))
then
partition=
df -kh | head -$i | tail -1| awk '{print $1}' TEXT="$partition at $(hostname -f) is ${percent}% full"
curl -s --max-time $TIMEOUT -d "chatid=$USERID&disablewebpagepreview=1&text=$TEXT" $URL > /dev/null
fi
let i=$i+1
done
https://redd.it/11qirwo
@r_bash
Reddit
r/bash on Reddit: bash noscript to send disk usage telegram alert
Posted by u/exstasi92 - No votes and 1 comment
My manager told me to execute this without any explenation on what it does. Anyone here has a clue?
Edit: Sorry, i know it's long, but I'm kinda worried on the nature of this noscript.
Also, noscript has typos, sorry.
@echo off
echo This noscript is for onboarding machines to the Microsoft Defender for Endpoint services, including security and compliance products.
echo Once completed, the machine should light up in the portal within 5-30 minutes, depending on this machine's Internet connectivity availability and machine power state (plugged in vs. battery powered).
echo IMPORTANT: This noscript is optimized for onboarding a single machine and should not be used for large scale deployment.
echo For more information on large scale deployment, please consult the MDE documentation (links available in the MDE portal under the endpoint onboarding section).
echo.
:USER_CONSENT
set /p shouldContinue= "Press (Y) to confirm and continue or (N) to cancel and exit: "
IF /I "%shouldContinue%"=="N" (
GOTO CLEANUP
)
IF /I "%shouldContinue%"=="Y" (
GOTO SCRIPT_START
)
echo.
echo Wrong input. Please try again.
GOTO USER_CONSENT
echo.
:SCRIPT_START
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v latency /t REG_SZ /f /d "Demo" >NUL 2>&1
@echo off
echo.
echo Starting Microsoft Defender for Endpoint onboarding process...
echo.
set errorCode=0
set lastError=0
set "troubleshootInfo=For more information, visit: https://go.microsoft.com/fwlink/p/?linkid=822807"
set "errorDenoscription="
echo Testing administrator privileges
net session >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
@echo Script is running with insufficient privileges. Please run with administrator privileges> %TMP%\senseTmp.txt
set errorCode=65
set lastError=%ERRORLEVEL%
GOTO ERROR
)
echo Script is running with sufficient privileges
echo.
echo Performing onboarding operations
echo.
IF [%PROCESSOR_ARCHITEW6432%] EQU [] (
set powershellPath=%windir%\System32\WindowsPowerShell\v1.0\powershell.exe
) ELSE (
set powershellPath=%windir%\SysNative\WindowsPowerShell\v1.0\powershell.exe
)
set sdbin=0100048044000000540000000000000014000000020030000200000000001400FF0F120001010000000000051200000000001400E104120001010000000000050B0000000102000000000005200000002002000001020000000000052000000020020000 >NUL 2>&1
reg add HKLM\SYSTEM\CurrentControlSet\Control\WMI\Security /v 14f8138e-3b61-580b-544b-2609378ae460 /t REG_BINARY /d %sdbin% /f >NUL 2>&1
reg add HKLM\SYSTEM\CurrentControlSet\Control\WMI\Security /v cb2ff72d-d4e4-585d-33f9-f3a395c40be7 /t REG_BINARY /d %sdbin% /f >NUL 2>&1
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows\DataCollection" /v DisableEnterpriseAuthProxy /t REG_DWORD /f /d 1 >NUL 2>&1
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type ' using System; using System.IO; using System.Runtime.InteropServices; using Microsoft.Win32.SafeHandles; using System.ComponentModel; public static class Elam{ [DllImport(\"Kernel32\", CharSet=CharSet.Auto, SetLastError=true)] public static extern bool InstallELAMCertificateInfo(SafeFileHandle handle); public static void InstallWdBoot(string path) { Console.Out.WriteLine(\"About to call create file on {0}\", path); var stream = File.Open(path, FileMode.Open, FileAccess.Read, FileShare.Read); var handle = stream.SafeFileHandle; Console.Out.WriteLine(\"About to call InstallELAMCertificateInfo on handle {0}\", handle.DangerousGetHandle()); if (!InstallELAMCertificateInfo(handle)) { Console.Out.WriteLine(\"Call failed.\"); throw new Win32Exception(Marshal.GetLastWin32Error()); } Console.Out.WriteLine(\"Call successful.\"); } } '; $driverPath = $env:SystemRoot + '\System32\Drivers\WdBoot.sys'; [Elam]::InstallWdBoot($driverPath) " >NUL 2>&1
REG query "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v
Edit: Sorry, i know it's long, but I'm kinda worried on the nature of this noscript.
Also, noscript has typos, sorry.
@echo off
echo This noscript is for onboarding machines to the Microsoft Defender for Endpoint services, including security and compliance products.
echo Once completed, the machine should light up in the portal within 5-30 minutes, depending on this machine's Internet connectivity availability and machine power state (plugged in vs. battery powered).
echo IMPORTANT: This noscript is optimized for onboarding a single machine and should not be used for large scale deployment.
echo For more information on large scale deployment, please consult the MDE documentation (links available in the MDE portal under the endpoint onboarding section).
echo.
:USER_CONSENT
set /p shouldContinue= "Press (Y) to confirm and continue or (N) to cancel and exit: "
IF /I "%shouldContinue%"=="N" (
GOTO CLEANUP
)
IF /I "%shouldContinue%"=="Y" (
GOTO SCRIPT_START
)
echo.
echo Wrong input. Please try again.
GOTO USER_CONSENT
echo.
:SCRIPT_START
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v latency /t REG_SZ /f /d "Demo" >NUL 2>&1
@echo off
echo.
echo Starting Microsoft Defender for Endpoint onboarding process...
echo.
set errorCode=0
set lastError=0
set "troubleshootInfo=For more information, visit: https://go.microsoft.com/fwlink/p/?linkid=822807"
set "errorDenoscription="
echo Testing administrator privileges
net session >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
@echo Script is running with insufficient privileges. Please run with administrator privileges> %TMP%\senseTmp.txt
set errorCode=65
set lastError=%ERRORLEVEL%
GOTO ERROR
)
echo Script is running with sufficient privileges
echo.
echo Performing onboarding operations
echo.
IF [%PROCESSOR_ARCHITEW6432%] EQU [] (
set powershellPath=%windir%\System32\WindowsPowerShell\v1.0\powershell.exe
) ELSE (
set powershellPath=%windir%\SysNative\WindowsPowerShell\v1.0\powershell.exe
)
set sdbin=0100048044000000540000000000000014000000020030000200000000001400FF0F120001010000000000051200000000001400E104120001010000000000050B0000000102000000000005200000002002000001020000000000052000000020020000 >NUL 2>&1
reg add HKLM\SYSTEM\CurrentControlSet\Control\WMI\Security /v 14f8138e-3b61-580b-544b-2609378ae460 /t REG_BINARY /d %sdbin% /f >NUL 2>&1
reg add HKLM\SYSTEM\CurrentControlSet\Control\WMI\Security /v cb2ff72d-d4e4-585d-33f9-f3a395c40be7 /t REG_BINARY /d %sdbin% /f >NUL 2>&1
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows\DataCollection" /v DisableEnterpriseAuthProxy /t REG_DWORD /f /d 1 >NUL 2>&1
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type ' using System; using System.IO; using System.Runtime.InteropServices; using Microsoft.Win32.SafeHandles; using System.ComponentModel; public static class Elam{ [DllImport(\"Kernel32\", CharSet=CharSet.Auto, SetLastError=true)] public static extern bool InstallELAMCertificateInfo(SafeFileHandle handle); public static void InstallWdBoot(string path) { Console.Out.WriteLine(\"About to call create file on {0}\", path); var stream = File.Open(path, FileMode.Open, FileAccess.Read, FileShare.Read); var handle = stream.SafeFileHandle; Console.Out.WriteLine(\"About to call InstallELAMCertificateInfo on handle {0}\", handle.DangerousGetHandle()); if (!InstallELAMCertificateInfo(handle)) { Console.Out.WriteLine(\"Call failed.\"); throw new Win32Exception(Marshal.GetLastWin32Error()); } Console.Out.WriteLine(\"Call successful.\"); } } '; $driverPath = $env:SystemRoot + '\System32\Drivers\WdBoot.sys'; [Elam]::InstallWdBoot($driverPath) " >NUL 2>&1
REG query "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v
Docs
Troubleshoot Microsoft Defender for Endpoint onboarding issues - Microsoft Defender for Endpoint
Troubleshoot issues that might arise during the onboarding of devices or to the Microsoft Defender for Endpoint service.
696C1FA1-4030-4FA4-8713-FAF9B2EA7C0A /reg:64 > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% EQU 0 (
REG delete "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v 696C1FA1-4030-4FA4-8713-FAF9B2EA7C0A /f > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% NEQ 0 (
set "errorDenoscription=Unable to delete previous offboarding information from registry."
set errorCode=5
set lastError=%ERRORLEVEL%
GOTO ERROR
)
)
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v OnboardingInfo /t REG_SZ /f /d
if %ERRORLEVEL% EQU 0 (
REG delete "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v 696C1FA1-4030-4FA4-8713-FAF9B2EA7C0A /f > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% NEQ 0 (
set "errorDenoscription=Unable to delete previous offboarding information from registry."
set errorCode=5
set lastError=%ERRORLEVEL%
GOTO ERROR
)
)
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v OnboardingInfo /t REG_SZ /f /d
"{\"body\":\"{\\\"previousOrgIds\\\":[],\\\"orgId\\\":\\\"6ad0aaaa-89b1-418b-934b-399c0ce86225\\\",\\\"geoLocationUrl\\\":\\\"https://winatp-gw-weu.microsoft.com/\\\",\\\"datacenter\\\":\\\"WestEurope\\\",\\\"vortexGeoLocation\\\":\\\"EU\\\",\\\"version\\\":\\\"1.45\\\"}\",\"sig\":\"dyzVy2wM1U9qjupC9HOqogWazgUr+8tdm+M8EcoOKDdfj9TItpL2o2rzZz1mpSD9a2X8FoA1w1HYV3zKE/xzxtx0xxSGPQdFz7la/slpttWqELKGIruE3GYYtWe0tgruqb73rX8nscPj3GCnnzVmLeIRqsWtWOMowMT/R8II7RuFGt51D+dHax4sKJ3VkkSumBVnL61p6nJboDy6htdidTCpkN83e7de9rBXBHMtI2SO5KvLahDqIHoHxulax43v0gM4BcGYZWMCHlBbwZrgPTdcs6H5G18SD7Wyctd6BEDx0t25xrYLHAs4nGlyHhDIhVh0Uyy+uclFjcrxjeajBA==\",\"sha256sig\":\"tjaopRgKg4efsSflwoy8wxymkYOxS2vvHStRwTLFTlLRqzeHq4OVWMV4YqYNhK1ofBkQky77LuVhdVsfwXuRTqPPrzimBgYBLKulCIe5p8s9vbYFbpCXxXxsLHui5LFBI4OORZ9p0Sxzth0AtDUdAjWcvaWWP5Y8b07fXnSRC/VjEOMBZrU+fAtJND/tYuZsBz4ZFJZ6xoPSO4nmoNtXbEh73V/bUkmezuLvxULXWRqiffOIGoPaZmdado/ext9Tu00rYRk1vmVeJXY8Q7D2eJypj4CHaw8OjcsyDMHnmrZf63mkHRi93CEt/XRmTuiPholB08NKtMmdQU9cEeyApg==\",\"cert\":\"MIIFgzCCA2ugAwIBAgITMwAAAgKh9Eww96dTKQAAAAACAjANBgkqhkiG9w0BAQsFADB+MQswCQYDVQQGEwJVUzETMBEGA1UECBMKV2FzaGluZ3RvbjEQMA4GA1UEBxMHUmVkbW9uZDEeMBwGA1UEChMVTWljcm9zb2Z0IENvcnBvcmF0aW9uMSgwJgYDVQQDEx9NaWNyb3NvZnQgU2VjdXJlIFNlcnZlciBDQSAyMDExMB4XDTIzMDIyMzE5NDMxMVoXDTI0MDIyMzE5NDMxMVowHjEcMBoGA1UEAxMTU2V2aWxsZS5XaW5kb3dzLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALjedJ4XjZjlasoG2AecXnOQ4T04l1VeqhjrfJ6PvQf1oiI8HuZ1l0l6Szgvl0yi2dehEL0llDAaqAjk/T5wFF6fYA4JfXriOTx83zsq9IKnjVZ34Jzbfkvy9lHTu+giCDkzs/Eo560rpJXl5VlGsQpzzYCkWZ6ZJQ1eDfrPqu3SISi+Na0cxE3nGpqG5mtMckdrsrzwrDuKm4qAQaGsGlfEoR1IVtCNydnuL+FmPK9+j/nzJ4eHqIzr8Euz3laW+UGvf2r7Z5n19IFT7sJuqjTeG5RC+LODHQFl/knG9sRQaae+zqkmPvMT7m4tx2/HJsyJsatOp38GJ3f+Qqy8/3UCAwEAAaOCAVgwggFUMA4GA1UdDwEB/wQEAwIFIDAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwDAYDVR0TAQH/BAIwADAeBgNVHREEFzAVghNTZXZpbGxlLldpbmRvd3MuY29tMB0GA1UdDgQWBBSz+8TlAUJCn2MDTDONsD1p+meKaTAfBgNVHSMEGDAWgBQ2VollSctbmy88rEIWUE2RuTPXkTBTBgNVHR8ETDBKMEigRqBEhkJodHRwOi8vd3d3Lm1pY3Jvc29mdC5jb20vcGtpb3BzL2NybC9NaWNTZWNTZXJDQTIwMTFfMjAxMS0xMC0xOC5jcmwwYAYIKwYBBQUHAQEEVDBSMFAGCCsGAQUFBzAChkRodHRwOi8vd3d3Lm1pY3Jvc29mdC5jb20vcGtpb3BzL2NlcnRzL01pY1NlY1NlckNBMjAxMV8yMDExLTEwLTE4LmNydDANBgkqhkiG9w0BAQsFAAOCAgEAoKKuLorfzJWL6HsBsAMwocM295/IkS5FVTASKTdZsqF9Q0Dvngx5YRMY1ljznNhyUYLXzLFKom2oVHlUmhbgY0zVkK798Mv6MEscMxxiQ9o/s8DxxdCBmnwswg3ERR8Q6RCqclsp8LEGUmQXJiLA5EFZSNMa2qlHQS3LoaEz5saVTvt6UihfwclY/F5MJOtlj+IJyv3lIX5Gdzi5wlCp7gMhOZmwDh2RCvulWT3wMmyz2lNT/vkEb8IJ7oKr+/oj7wPTmCZ0k20wyDIa9QbVBMX0CiotY5RHkHZnzkpi4lWc6f2MXsqMRjP6iyyylWQ1Itn+rKjHeBuLAIfqQWuvfT1kyH5IM6QXQw8DS6Wto0hjIx9epUOPscxOr/Qli8zOYJ3i/h3j9/x41hArCnla/ISf5hDVPm0/LTDfFZWxuvMjjnkk+HmsEpq5oaV/Pmuh8ml47kXWddJrAJGDPtEZNqpjO+ObH0P7kb/t5feK1mTmSsKwMJVTnlIUuubbRM2ZeQ0kkZKSUhVjMvO6YfoR6f2EkrCXWlr9VPYtro+pAy4cVMARDW1aOPPLyxk/7cLL+YUTYbEOw+D+bQXEr00AsjmzucvRN2paejjBSH8A+8k+alPobReH88Ktlo4GkqbK9S3vSqH4zJC3GcIJ+mQBxcUlmKWbC5lRo9btWPcTEOU=\",\"chain\":[\"MIIG2DCCBMCgAwIBAgIKYT+3GAAAAAAABDANBgkqhkiG9w0BAQsFADCBiDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCldhc2hpbmd0b24xEDAOBgNVBAcTB1JlZG1vbmQxHjAcBgNVBAoTFU1pY3Jvc29mdCBDb3Jwb3JhdGlvbjEyMDAGA1UEAxMpTWljcm9zb2Z0IFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IDIwMTEwHhcNMTExMDE4MjI1NTE5WhcNMjYxMDE4MjMwNTE5WjB+MQswCQYDVQQGEwJVUzETMBEGA1UECBMKV2FzaGluZ3RvbjEQMA4GA1UEBxMHUmVkbW9uZDEeMBwGA1UEChMVTWljcm9zb2Z0IENvcnBvcmF0aW9uMSgwJgYDVQQDEx9NaWNyb3NvZnQgU2VjdXJlIFNlcnZlciBDQSAyMDExMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA0AvApKgZgeI25eKq5fOyFVh1vrTlSfHghPm7DWTvhcGBVbjz5/FtQFU9zotq0YST9XV8W6TUdBDKMvMj067uz54EWMLZR8vRfABBSHEbAWcXGK/G/nMDfuTvQ5zvAXEqH4EmQ3eYVFdznVUr8J6OfQYOrBtU8yb3+CMIIoueBh03OP1y0srlY8GaWn2ybbNSqW7prrX8izb5nvr2HFgbl1alEeW3Utu76fBUv7T/LGy4XSbOoArX35Ptf92s8SxzGtkZN1W63SJ4jqHUmwn4ByIxcbCUruCw5yZEV5CBlxXOYexl4kvxhVIWMvi1eKp+zU3sgyGkqJu+mmoE4KMczVYYbP1rL0I+4jfycqvQeHNye97sAFjlITCjCDqZ75/D93oWlmW1w4Gv9DlwSa/2qfZqADj5tAgZ4Bo1pVZ2Il9q8mmuPq1YRk24VPaJQUQecrG8EidT0sH/ss1QmB619Lu2woI52awb8jsnhGqwxiYL1zoQ57PbfNNWrFNMC/o7MTd02Fkr+QB5GQZ7/RwdQtRBDS8FDtVrSSP/z834eoLP2jwt3+jYEgQYuh6Id7iYHxAHu8gFfgsJv2vd405bsPnHhKY7ykyfW2Ip98eiqJWIcCzlwT88UiNPQJrDMYWDL78p8R1QjyGWB87v8oDCRH2bYu8vw3eJq0VNUz4CedMCAwEAAaO
CAUswggFHMBAGCSsGAQQBgjcVAQQDAgEAMB0GA1UdDgQWBBQ2VollSctbmy88rEIWUE2RuTPXkTAZBgkrBgEEAYI3FAIEDB4KAFMAdQBiAEMAQTALBgNVHQ8EBAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAfBgNVHSMEGDAWgBRyLToCMZBDuRQFTuHqp8cx0SOJNDBaBgNVHR8EUzBRME+gTaBLhklodHRwOi8vY3JsLm1pY3Jvc29mdC5jb20vcGtpL2NybC9wcm9kdWN0cy9NaWNSb29DZXJBdXQyMDExXzIwMTFfMDNfMjIuY3JsMF4GCCsGAQUFBwEBBFIwUDBOBggrBgEFBQcwAoZCaHR0cDovL3d3dy5taWNyb3NvZnQuY29tL3BraS9jZXJ0cy9NaWNSb29DZXJBdXQyMDExXzIwMTFfMDNfMjIuY3J0MA0GCSqGSIb3DQEBCwUAA4ICAQBByGHB9VuePpEx8bDGvwkBtJ22kHTXCdumLg2fyOd2NEavB2CJTIGzPNX0EjV1wnOl9U2EjMukXa+/kvYXCFdClXJlBXZ5re7RurguVKNRB6xo6yEM4yWBws0q8sP/z8K9SRiax/CExfkUvGuV5Zbvs0LSU9VKoBLErhJ2UwlWDp3306ZJiFDyiiyXIKK+TnjvBWW3S6EWiN4xxwhCJHyke56dvGAAXmKX45P8p/5beyXf5FN/S77mPvDbAXlCHG6FbH22RDD7pTeSk7Kl7iCtP1PVyfQoa1fB+B1qt1YqtieBHKYtn+f00DGDl6gqtqy+G0H15IlfVvvaWtNefVWUEH5TV/RKPUAqyL1nn4ThEO792msVgkn8Rh3/RQZ0nEIU7cU507PNC4MnkENRkvJEgq5umhUXshn6x0VsmAF7vzepsIikkrw4OOAd5HyXmBouX+84Zbc1L71/TyH6xIzSbwb5STXq3yAPJarqYKssH0uJ/Lf6XFSQSz6iKE9s5FJlwf2QHIWCiG7pplXdISh5RbAU5QrM5l/Eu9thNGmfrCY498EpQQgVLkyg9/kMPt5fqwgJLYOsrDSDYvTJSUKJJbVuskfFszmgsSAbLLGOBG+lMEkc0EbpQFv0rW6624JKhxJKgAlN2992uQVbG+C7IHBfACXH0w76Fq17Ip5xCA==\",\"MIIF7TCCA9WgAwIBAgIQP4vItfyfspZDtWnWbELhRDANBgkqhkiG9w0BAQsFADCBiDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCldhc2hpbmd0b24xEDAOBgNVBAcTB1JlZG1vbmQxHjAcBgNVBAoTFU1pY3Jvc29mdCBDb3Jwb3JhdGlvbjEyMDAGA1UEAxMpTWljcm9zb2Z0IFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IDIwMTEwHhcNMTEwMzIyMjIwNTI4WhcNMzYwMzIyMjIxMzA0WjCBiDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCldhc2hpbmd0b24xEDAOBgNVBAcTB1JlZG1vbmQxHjAcBgNVBAoTFU1pY3Jvc29mdCBDb3Jwb3JhdGlvbjEyMDAGA1UEAxMpTWljcm9zb2Z0IFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IDIwMTEwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCygEGqNThNE3IyaCJNuLLx/9VSvGzH9dJKjDbu0cJcfoyKrq8TKG/Ac+M6ztAlqFo6be+ouFmrEyNozQwph9FvgFyPRH9dkAFSWKxRxV8qh9zc2AodwQO5e7BW6KPeZGHCnvjzfLnsDbVU/ky2ZU+I8JxImQxCCwl8MVkXeQZ4KI2JOkwDJb5xalwL54RgpJki49KvhKSn+9GY7Qyp3pSJ4Q6g3MDOmT3qCFK7VnnkH4S6Hri0xElcTzFLh93dBWcmmYDgcRGjuKVB4qRTufcyKYMME782XgSzS0NHL2vikR7TmE/dQgfI6B0S/Jmpaz6SfsjWaTr8ZL22CZ3K/QwLopt3YEsDlKQwaRLWQi3BQUzK3Kr9j1uDRprZ/LHR47PJf0h6zSTwQY9cdNCssBAgBkm3xy0hyFfj0IbzA2j70M5xwYmZSmQBbP3sMJHPQTySx+W6hh1hhMdfgzlirrSSL0fzC/hV66AfWdC7dJse0Hbm8ukG1xDo+mTeacY1logC8Ea4PyeZb8txiSk190gWAjWP1Xl8TQLPX+uKg09FcYj5qQ1OcunCnAfPSRtOBA5jUYxe2ADBVSy2xuDCZU7JNDn1nLPEfuhhbhNfFcRf2X7tHc7uROzLLoax7Dj2cO2rXBPB2Q8Nx4CyVe0096yb5MPa50c8prWPMd/FS6/r8QIDAQABo1EwTzALBgNVHQ8EBAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUci06AjGQQ7kUBU7h6qfHMdEjiTQwEAYJKwYBBAGCNxUBBAMCAQAwDQYJKoZIhvcNAQELBQADggIBAH9yzw+3xRXbm8BJyiZb/p4T5tPw0tuXX/JLP02zrhmu7deXoKzvqTqjwkGw5biRnhOBJAPmCf0/V0A5ISRW0RAvS0CpNoZLtFNXmvvxfomPEf4YbFGq6O0JlbXlccmh6Yd1phV/yX43VF50k8XDZ8wNT2uoFwxtCJJ+i92Bqi1wIcM9BhS7vyRep4TXPw8hIr1LAAbblxzYXtTFC1yHblCk6MM4pPvLLMWSZpuFXst6bJN8gClYW1e1QGm6CHmmZGIVnYeWRbVmIyADixxzoNOieTPgUFmG2y/lAiXqcyqfABTINseSO+lOAOzYVgm5M0kS0lQLAausR7aRKX1MtHWAUgHoyoL2n8ysnI8X6i8msKtyrAv+nlEex0NVZ09Rs1fWtuzuUrc66U7h14GIvE+OdbtLqPA1qibUZ2dJsnBMO5PcHd94kIZysjik0dySTclY6ysSXNQ7roxrsIPlAT/4CTL2kzU0Iq/dNw13CYArzUgA8YyZGUcFAenRv9FO0OYoQzeZpApKCNmacXPSqs0xE2N2oTdvkjgefRI8ZjLny23h/FKJ3crWZgWalmG+oijHHKOnNlA8OqTfSm7mhzvO6/DggTedEzxSjr25HTTGHdUKaj2YKXCMiSrRq4IQSB/c9O+lxbtVGjhjhE63bK2VVOxlIhBJF7jAHscPrFRH\"]}" > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% NEQ 0 (
set "errorDenoscription=Unable to write onboarding information to registry."
set errorCode=10
set lastError=%ERRORLEVEL%
GOTO ERROR
)
echo Starting the service, if not already running
echo.
sc query "SENSE" | find /i "RUNNING" >NUL 2>&1
if %ERRORLEVEL% EQU 0 GOTO RUNNING
net start sense > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% NEQ 0 (
echo Microsoft Defender for Endpoint Service has not started yet
GOTO WAIT_FOR_THE_SERVICE_TO_START
)
goto SUCCEEDED
:RUNNING
set "runningOutput=The Microsoft Defender for Endpoint Service is already running!"
echo %runningOutput%
echo.
eventcreate /l Application /so WDATPOnboarding /t Information /id 10 /d "%runningOutput%" >NUL 2>&1
GOTO WAIT_FOR_THE_SERVICE_TO_START
:ERROR
if %ERRORLEVEL% NEQ 0 (
set "errorDenoscription=Unable to write onboarding information to registry."
set errorCode=10
set lastError=%ERRORLEVEL%
GOTO ERROR
)
echo Starting the service, if not already running
echo.
sc query "SENSE" | find /i "RUNNING" >NUL 2>&1
if %ERRORLEVEL% EQU 0 GOTO RUNNING
net start sense > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% NEQ 0 (
echo Microsoft Defender for Endpoint Service has not started yet
GOTO WAIT_FOR_THE_SERVICE_TO_START
)
goto SUCCEEDED
:RUNNING
set "runningOutput=The Microsoft Defender for Endpoint Service is already running!"
echo %runningOutput%
echo.
eventcreate /l Application /so WDATPOnboarding /t Information /id 10 /d "%runningOutput%" >NUL 2>&1
GOTO WAIT_FOR_THE_SERVICE_TO_START
:ERROR
Set /P errorMsg=<%TMP%\senseTmp.txt
set "errorOutput=[Error Id: %errorCode%, Error Level: %lastError%] %errorDenoscription% Error message: %errorMsg%"
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type 'using System; using System.Diagnostics; using System.Diagnostics.Tracing; namespace Sense { [EventData(Name = \"Onboarding\")]public struct Onboarding{public string Message { get; set; }} public class Trace {public static EventSourceOptions TelemetryCriticalOption = new EventSourceOptions(){Level = EventLevel.Error, Keywords = (EventKeywords)0x0000200000000000, Tags = (EventTags)0x0200000}; public void WriteOnboardingMessage(string message){es.Write(\"OnboardingScript\", TelemetryCriticalOption, new Onboarding {Message = message});} private static readonly string[] telemetryTraits = { \"ETW_GROUP\", \"{5ECB0BAC-B930-47F5-A8A4-E8253529EDB7}\" }; private EventSource es = new EventSource(\"Microsoft.Windows.Sense.Client.Management\",EventSourceSettings.EtwSelfDescribingEventFormat,telemetryTraits);}}'; $logger = New-Object -TypeName Sense.Trace; $logger.WriteOnboardingMessage('%errorOutput%')" >NUL 2>&1
echo %errorOutput%
echo %troubleshootInfo%
echo.
eventcreate /l Application /so WDATPOnboarding /t Error /id %errorCode% /d "%errorOutput%" >NUL 2>&1
GOTO CLEANUP
:SUCCEEDED
echo Finished performing onboarding operations
echo.
GOTO WAIT_FOR_THE_SERVICE_TO_START
:WAIT_FOR_THE_SERVICE_TO_START
echo Waiting for the service to start
echo.
set /a counter=0
:SENSE_RUNNING_WAIT
sc query "SENSE" | find /i "RUNNING" >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
set "errorDenoscription=Unable to start Microsoft Defender for Endpoint Service."
set errorCode=15
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_RUNNING_WAIT
)
set /a counter=0
:SENSE_ONBOARDED_STATUS_WAIT
REG query "HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status" /v OnboardingState /reg:64 >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
@echo Microsoft Defender for Endpoint Service is not running as expected> %TMP%\senseTmp.txt
set errorCode=35
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_ONBOARDED_STATUS_WAIT
)
set /a counter=0
:SENSE_ONBOARDED_WAIT
REG query "HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status" /v OnboardingState /reg:64 | find /i "0x1" >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
@echo Microsoft Defender for Endpoint Service is not running as expected> %TMP%\senseTmp.txt
set errorCode=40
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_ONBOARDED_WAIT
)
set "successOutput=Successfully onboarded machine to Microsoft Defender for Endpoint"
echo %successOutput%
echo.
eventcreate /l Application /so WDATPOnboarding /t Information /id 20 /d "%successOutput%" >NUL 2>&1
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type 'using System; using System.Diagnostics; using System.Diagnostics.Tracing; namespace Sense { [EventData(Name = \"Onboarding\")]public struct Onboarding{public string Message { get; set; }} public class Trace {public static EventSourceOptions TelemetryCriticalOption = new EventSourceOptions(){Level = EventLevel.Informational, Keywords = (EventKeywords)0x0000200000000000, Tags = (EventTags)0x0200000}; public void WriteOnboardingMessage(string message){es.Write(\"OnboardingScript\", TelemetryCriticalOption, new Onboarding {Message = message});} private static readonly string[] telemetryTraits = { \"ETW_GROUP\", \"{5ECB0BAC-B930-47F5-A8A4-E8253529EDB7}\" }; private EventSource es = new
set "errorOutput=[Error Id: %errorCode%, Error Level: %lastError%] %errorDenoscription% Error message: %errorMsg%"
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type 'using System; using System.Diagnostics; using System.Diagnostics.Tracing; namespace Sense { [EventData(Name = \"Onboarding\")]public struct Onboarding{public string Message { get; set; }} public class Trace {public static EventSourceOptions TelemetryCriticalOption = new EventSourceOptions(){Level = EventLevel.Error, Keywords = (EventKeywords)0x0000200000000000, Tags = (EventTags)0x0200000}; public void WriteOnboardingMessage(string message){es.Write(\"OnboardingScript\", TelemetryCriticalOption, new Onboarding {Message = message});} private static readonly string[] telemetryTraits = { \"ETW_GROUP\", \"{5ECB0BAC-B930-47F5-A8A4-E8253529EDB7}\" }; private EventSource es = new EventSource(\"Microsoft.Windows.Sense.Client.Management\",EventSourceSettings.EtwSelfDescribingEventFormat,telemetryTraits);}}'; $logger = New-Object -TypeName Sense.Trace; $logger.WriteOnboardingMessage('%errorOutput%')" >NUL 2>&1
echo %errorOutput%
echo %troubleshootInfo%
echo.
eventcreate /l Application /so WDATPOnboarding /t Error /id %errorCode% /d "%errorOutput%" >NUL 2>&1
GOTO CLEANUP
:SUCCEEDED
echo Finished performing onboarding operations
echo.
GOTO WAIT_FOR_THE_SERVICE_TO_START
:WAIT_FOR_THE_SERVICE_TO_START
echo Waiting for the service to start
echo.
set /a counter=0
:SENSE_RUNNING_WAIT
sc query "SENSE" | find /i "RUNNING" >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
set "errorDenoscription=Unable to start Microsoft Defender for Endpoint Service."
set errorCode=15
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_RUNNING_WAIT
)
set /a counter=0
:SENSE_ONBOARDED_STATUS_WAIT
REG query "HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status" /v OnboardingState /reg:64 >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
@echo Microsoft Defender for Endpoint Service is not running as expected> %TMP%\senseTmp.txt
set errorCode=35
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_ONBOARDED_STATUS_WAIT
)
set /a counter=0
:SENSE_ONBOARDED_WAIT
REG query "HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status" /v OnboardingState /reg:64 | find /i "0x1" >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
@echo Microsoft Defender for Endpoint Service is not running as expected> %TMP%\senseTmp.txt
set errorCode=40
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_ONBOARDED_WAIT
)
set "successOutput=Successfully onboarded machine to Microsoft Defender for Endpoint"
echo %successOutput%
echo.
eventcreate /l Application /so WDATPOnboarding /t Information /id 20 /d "%successOutput%" >NUL 2>&1
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type 'using System; using System.Diagnostics; using System.Diagnostics.Tracing; namespace Sense { [EventData(Name = \"Onboarding\")]public struct Onboarding{public string Message { get; set; }} public class Trace {public static EventSourceOptions TelemetryCriticalOption = new EventSourceOptions(){Level = EventLevel.Informational, Keywords = (EventKeywords)0x0000200000000000, Tags = (EventTags)0x0200000}; public void WriteOnboardingMessage(string message){es.Write(\"OnboardingScript\", TelemetryCriticalOption, new Onboarding {Message = message});} private static readonly string[] telemetryTraits = { \"ETW_GROUP\", \"{5ECB0BAC-B930-47F5-A8A4-E8253529EDB7}\" }; private EventSource es = new
EventSource(\"Microsoft.Windows.Sense.Client.Management\",EventSourceSettings.EtwSelfDescribingEventFormat,telemetryTraits);}}'; $logger = New-Object -TypeName Sense.Trace; $logger.WriteOnboardingMessage('%successOutput%')" >NUL 2>&1
"%PROGRAMFILES%\Windows Defender\MpCmdRun.exe" -ReloadEngine >NUL 2>&1
GOTO CLEANUP
:CLEANUP
if exist %TMP%\senseTmp.txt del %TMP%\senseTmp.txt
pause
EXIT /B %errorCode%
https://redd.it/11qxe60
@r_bash
"%PROGRAMFILES%\Windows Defender\MpCmdRun.exe" -ReloadEngine >NUL 2>&1
GOTO CLEANUP
:CLEANUP
if exist %TMP%\senseTmp.txt del %TMP%\senseTmp.txt
pause
EXIT /B %errorCode%
https://redd.it/11qxe60
@r_bash
Reddit
r/bash on Reddit: My manager told me to execute this without any explenation on what it does. Anyone here has a clue?
Posted by u/ya-boi-moe - No votes and no comments
I made a bash noscript to fetch all Android System Info in the termux app, Any Suggestions can be helpful to improve the noscript.
https://redd.it/11r1x2y
@r_bash
https://redd.it/11r1x2y
@r_bash
Reddit
r/bash on Reddit: I made a bash noscript to fetch all Android System Info in the termux app, Any Suggestions can be helpful to improve…
Posted by u/A_J07 - No votes and no comments