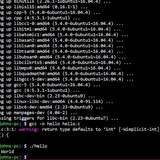
Cannot match character limit with regex
I have a bit of regex I'm struggling with and cannot seem to get it to only allow up to 20 characters.
I want it to match either with max of 20 characters in length:
I do not want it to match:
This is what I have:
What's wrong with this?
https://redd.it/11qihgm
@r_bash
I have a bit of regex I'm struggling with and cannot seem to get it to only allow up to 20 characters.
I want it to match either with max of 20 characters in length:
test test-123 I do not want it to match:
test- -test test-123- This is what I have:
^([A-Za-z0-9]+)([-A-Za-z0-9]*)([A-Za-z0-9]+).{1,20}$'What's wrong with this?
https://redd.it/11qihgm
@r_bash
Reddit
r/bash on Reddit: Cannot match character limit with regex
Posted by u/bluegreen456 - No votes and no comments
bash noscript to send disk usage telegram alert
Hello, I have found this interesting noscript googling but it gives me error on line 12 ans 18 percent not found and let not found. Can someone help me fixing it ?
#!/bin/bash
USERID="XXX" #Chat to u/getidbot
KEY="XXX" #Telegram Secret Code
URL="https://api.telegram.org/bot$KEY/sendMessage"
TIMEOUT="10"
threshold="90" #Set Custom Threshold
i=2
result=
for percent in $result; do
if ((percent > threshold))
then
partition=
TEXT="$partition at $(hostname -f) is ${percent}% full"
curl -s --max-time $TIMEOUT -d "chatid=$USERID&disablewebpagepreview=1&text=$TEXT" $URL > /dev/null
fi
let i=$i+1
done
https://redd.it/11qirwo
@r_bash
Hello, I have found this interesting noscript googling but it gives me error on line 12 ans 18 percent not found and let not found. Can someone help me fixing it ?
#!/bin/bash
USERID="XXX" #Chat to u/getidbot
KEY="XXX" #Telegram Secret Code
URL="https://api.telegram.org/bot$KEY/sendMessage"
TIMEOUT="10"
threshold="90" #Set Custom Threshold
i=2
result=
df -kh /dev/sda1 |grep -v "Filesystem" | awk '{ print $5 }' | sed 's/%//g' for percent in $result; do
if ((percent > threshold))
then
partition=
df -kh | head -$i | tail -1| awk '{print $1}' TEXT="$partition at $(hostname -f) is ${percent}% full"
curl -s --max-time $TIMEOUT -d "chatid=$USERID&disablewebpagepreview=1&text=$TEXT" $URL > /dev/null
fi
let i=$i+1
done
https://redd.it/11qirwo
@r_bash
Reddit
r/bash on Reddit: bash noscript to send disk usage telegram alert
Posted by u/exstasi92 - No votes and 1 comment
My manager told me to execute this without any explenation on what it does. Anyone here has a clue?
Edit: Sorry, i know it's long, but I'm kinda worried on the nature of this noscript.
Also, noscript has typos, sorry.
@echo off
echo This noscript is for onboarding machines to the Microsoft Defender for Endpoint services, including security and compliance products.
echo Once completed, the machine should light up in the portal within 5-30 minutes, depending on this machine's Internet connectivity availability and machine power state (plugged in vs. battery powered).
echo IMPORTANT: This noscript is optimized for onboarding a single machine and should not be used for large scale deployment.
echo For more information on large scale deployment, please consult the MDE documentation (links available in the MDE portal under the endpoint onboarding section).
echo.
:USER_CONSENT
set /p shouldContinue= "Press (Y) to confirm and continue or (N) to cancel and exit: "
IF /I "%shouldContinue%"=="N" (
GOTO CLEANUP
)
IF /I "%shouldContinue%"=="Y" (
GOTO SCRIPT_START
)
echo.
echo Wrong input. Please try again.
GOTO USER_CONSENT
echo.
:SCRIPT_START
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v latency /t REG_SZ /f /d "Demo" >NUL 2>&1
@echo off
echo.
echo Starting Microsoft Defender for Endpoint onboarding process...
echo.
set errorCode=0
set lastError=0
set "troubleshootInfo=For more information, visit: https://go.microsoft.com/fwlink/p/?linkid=822807"
set "errorDenoscription="
echo Testing administrator privileges
net session >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
@echo Script is running with insufficient privileges. Please run with administrator privileges> %TMP%\senseTmp.txt
set errorCode=65
set lastError=%ERRORLEVEL%
GOTO ERROR
)
echo Script is running with sufficient privileges
echo.
echo Performing onboarding operations
echo.
IF [%PROCESSOR_ARCHITEW6432%] EQU [] (
set powershellPath=%windir%\System32\WindowsPowerShell\v1.0\powershell.exe
) ELSE (
set powershellPath=%windir%\SysNative\WindowsPowerShell\v1.0\powershell.exe
)
set sdbin=0100048044000000540000000000000014000000020030000200000000001400FF0F120001010000000000051200000000001400E104120001010000000000050B0000000102000000000005200000002002000001020000000000052000000020020000 >NUL 2>&1
reg add HKLM\SYSTEM\CurrentControlSet\Control\WMI\Security /v 14f8138e-3b61-580b-544b-2609378ae460 /t REG_BINARY /d %sdbin% /f >NUL 2>&1
reg add HKLM\SYSTEM\CurrentControlSet\Control\WMI\Security /v cb2ff72d-d4e4-585d-33f9-f3a395c40be7 /t REG_BINARY /d %sdbin% /f >NUL 2>&1
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows\DataCollection" /v DisableEnterpriseAuthProxy /t REG_DWORD /f /d 1 >NUL 2>&1
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type ' using System; using System.IO; using System.Runtime.InteropServices; using Microsoft.Win32.SafeHandles; using System.ComponentModel; public static class Elam{ [DllImport(\"Kernel32\", CharSet=CharSet.Auto, SetLastError=true)] public static extern bool InstallELAMCertificateInfo(SafeFileHandle handle); public static void InstallWdBoot(string path) { Console.Out.WriteLine(\"About to call create file on {0}\", path); var stream = File.Open(path, FileMode.Open, FileAccess.Read, FileShare.Read); var handle = stream.SafeFileHandle; Console.Out.WriteLine(\"About to call InstallELAMCertificateInfo on handle {0}\", handle.DangerousGetHandle()); if (!InstallELAMCertificateInfo(handle)) { Console.Out.WriteLine(\"Call failed.\"); throw new Win32Exception(Marshal.GetLastWin32Error()); } Console.Out.WriteLine(\"Call successful.\"); } } '; $driverPath = $env:SystemRoot + '\System32\Drivers\WdBoot.sys'; [Elam]::InstallWdBoot($driverPath) " >NUL 2>&1
REG query "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v
Edit: Sorry, i know it's long, but I'm kinda worried on the nature of this noscript.
Also, noscript has typos, sorry.
@echo off
echo This noscript is for onboarding machines to the Microsoft Defender for Endpoint services, including security and compliance products.
echo Once completed, the machine should light up in the portal within 5-30 minutes, depending on this machine's Internet connectivity availability and machine power state (plugged in vs. battery powered).
echo IMPORTANT: This noscript is optimized for onboarding a single machine and should not be used for large scale deployment.
echo For more information on large scale deployment, please consult the MDE documentation (links available in the MDE portal under the endpoint onboarding section).
echo.
:USER_CONSENT
set /p shouldContinue= "Press (Y) to confirm and continue or (N) to cancel and exit: "
IF /I "%shouldContinue%"=="N" (
GOTO CLEANUP
)
IF /I "%shouldContinue%"=="Y" (
GOTO SCRIPT_START
)
echo.
echo Wrong input. Please try again.
GOTO USER_CONSENT
echo.
:SCRIPT_START
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v latency /t REG_SZ /f /d "Demo" >NUL 2>&1
@echo off
echo.
echo Starting Microsoft Defender for Endpoint onboarding process...
echo.
set errorCode=0
set lastError=0
set "troubleshootInfo=For more information, visit: https://go.microsoft.com/fwlink/p/?linkid=822807"
set "errorDenoscription="
echo Testing administrator privileges
net session >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
@echo Script is running with insufficient privileges. Please run with administrator privileges> %TMP%\senseTmp.txt
set errorCode=65
set lastError=%ERRORLEVEL%
GOTO ERROR
)
echo Script is running with sufficient privileges
echo.
echo Performing onboarding operations
echo.
IF [%PROCESSOR_ARCHITEW6432%] EQU [] (
set powershellPath=%windir%\System32\WindowsPowerShell\v1.0\powershell.exe
) ELSE (
set powershellPath=%windir%\SysNative\WindowsPowerShell\v1.0\powershell.exe
)
set sdbin=0100048044000000540000000000000014000000020030000200000000001400FF0F120001010000000000051200000000001400E104120001010000000000050B0000000102000000000005200000002002000001020000000000052000000020020000 >NUL 2>&1
reg add HKLM\SYSTEM\CurrentControlSet\Control\WMI\Security /v 14f8138e-3b61-580b-544b-2609378ae460 /t REG_BINARY /d %sdbin% /f >NUL 2>&1
reg add HKLM\SYSTEM\CurrentControlSet\Control\WMI\Security /v cb2ff72d-d4e4-585d-33f9-f3a395c40be7 /t REG_BINARY /d %sdbin% /f >NUL 2>&1
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows\DataCollection" /v DisableEnterpriseAuthProxy /t REG_DWORD /f /d 1 >NUL 2>&1
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type ' using System; using System.IO; using System.Runtime.InteropServices; using Microsoft.Win32.SafeHandles; using System.ComponentModel; public static class Elam{ [DllImport(\"Kernel32\", CharSet=CharSet.Auto, SetLastError=true)] public static extern bool InstallELAMCertificateInfo(SafeFileHandle handle); public static void InstallWdBoot(string path) { Console.Out.WriteLine(\"About to call create file on {0}\", path); var stream = File.Open(path, FileMode.Open, FileAccess.Read, FileShare.Read); var handle = stream.SafeFileHandle; Console.Out.WriteLine(\"About to call InstallELAMCertificateInfo on handle {0}\", handle.DangerousGetHandle()); if (!InstallELAMCertificateInfo(handle)) { Console.Out.WriteLine(\"Call failed.\"); throw new Win32Exception(Marshal.GetLastWin32Error()); } Console.Out.WriteLine(\"Call successful.\"); } } '; $driverPath = $env:SystemRoot + '\System32\Drivers\WdBoot.sys'; [Elam]::InstallWdBoot($driverPath) " >NUL 2>&1
REG query "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v
Docs
Troubleshoot Microsoft Defender for Endpoint onboarding issues - Microsoft Defender for Endpoint
Troubleshoot issues that might arise during the onboarding of devices or to the Microsoft Defender for Endpoint service.
696C1FA1-4030-4FA4-8713-FAF9B2EA7C0A /reg:64 > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% EQU 0 (
REG delete "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v 696C1FA1-4030-4FA4-8713-FAF9B2EA7C0A /f > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% NEQ 0 (
set "errorDenoscription=Unable to delete previous offboarding information from registry."
set errorCode=5
set lastError=%ERRORLEVEL%
GOTO ERROR
)
)
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v OnboardingInfo /t REG_SZ /f /d
if %ERRORLEVEL% EQU 0 (
REG delete "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v 696C1FA1-4030-4FA4-8713-FAF9B2EA7C0A /f > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% NEQ 0 (
set "errorDenoscription=Unable to delete previous offboarding information from registry."
set errorCode=5
set lastError=%ERRORLEVEL%
GOTO ERROR
)
)
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection" /v OnboardingInfo /t REG_SZ /f /d
"{\"body\":\"{\\\"previousOrgIds\\\":[],\\\"orgId\\\":\\\"6ad0aaaa-89b1-418b-934b-399c0ce86225\\\",\\\"geoLocationUrl\\\":\\\"https://winatp-gw-weu.microsoft.com/\\\",\\\"datacenter\\\":\\\"WestEurope\\\",\\\"vortexGeoLocation\\\":\\\"EU\\\",\\\"version\\\":\\\"1.45\\\"}\",\"sig\":\"dyzVy2wM1U9qjupC9HOqogWazgUr+8tdm+M8EcoOKDdfj9TItpL2o2rzZz1mpSD9a2X8FoA1w1HYV3zKE/xzxtx0xxSGPQdFz7la/slpttWqELKGIruE3GYYtWe0tgruqb73rX8nscPj3GCnnzVmLeIRqsWtWOMowMT/R8II7RuFGt51D+dHax4sKJ3VkkSumBVnL61p6nJboDy6htdidTCpkN83e7de9rBXBHMtI2SO5KvLahDqIHoHxulax43v0gM4BcGYZWMCHlBbwZrgPTdcs6H5G18SD7Wyctd6BEDx0t25xrYLHAs4nGlyHhDIhVh0Uyy+uclFjcrxjeajBA==\",\"sha256sig\":\"tjaopRgKg4efsSflwoy8wxymkYOxS2vvHStRwTLFTlLRqzeHq4OVWMV4YqYNhK1ofBkQky77LuVhdVsfwXuRTqPPrzimBgYBLKulCIe5p8s9vbYFbpCXxXxsLHui5LFBI4OORZ9p0Sxzth0AtDUdAjWcvaWWP5Y8b07fXnSRC/VjEOMBZrU+fAtJND/tYuZsBz4ZFJZ6xoPSO4nmoNtXbEh73V/bUkmezuLvxULXWRqiffOIGoPaZmdado/ext9Tu00rYRk1vmVeJXY8Q7D2eJypj4CHaw8OjcsyDMHnmrZf63mkHRi93CEt/XRmTuiPholB08NKtMmdQU9cEeyApg==\",\"cert\":\"MIIFgzCCA2ugAwIBAgITMwAAAgKh9Eww96dTKQAAAAACAjANBgkqhkiG9w0BAQsFADB+MQswCQYDVQQGEwJVUzETMBEGA1UECBMKV2FzaGluZ3RvbjEQMA4GA1UEBxMHUmVkbW9uZDEeMBwGA1UEChMVTWljcm9zb2Z0IENvcnBvcmF0aW9uMSgwJgYDVQQDEx9NaWNyb3NvZnQgU2VjdXJlIFNlcnZlciBDQSAyMDExMB4XDTIzMDIyMzE5NDMxMVoXDTI0MDIyMzE5NDMxMVowHjEcMBoGA1UEAxMTU2V2aWxsZS5XaW5kb3dzLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBALjedJ4XjZjlasoG2AecXnOQ4T04l1VeqhjrfJ6PvQf1oiI8HuZ1l0l6Szgvl0yi2dehEL0llDAaqAjk/T5wFF6fYA4JfXriOTx83zsq9IKnjVZ34Jzbfkvy9lHTu+giCDkzs/Eo560rpJXl5VlGsQpzzYCkWZ6ZJQ1eDfrPqu3SISi+Na0cxE3nGpqG5mtMckdrsrzwrDuKm4qAQaGsGlfEoR1IVtCNydnuL+FmPK9+j/nzJ4eHqIzr8Euz3laW+UGvf2r7Z5n19IFT7sJuqjTeG5RC+LODHQFl/knG9sRQaae+zqkmPvMT7m4tx2/HJsyJsatOp38GJ3f+Qqy8/3UCAwEAAaOCAVgwggFUMA4GA1UdDwEB/wQEAwIFIDAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwDAYDVR0TAQH/BAIwADAeBgNVHREEFzAVghNTZXZpbGxlLldpbmRvd3MuY29tMB0GA1UdDgQWBBSz+8TlAUJCn2MDTDONsD1p+meKaTAfBgNVHSMEGDAWgBQ2VollSctbmy88rEIWUE2RuTPXkTBTBgNVHR8ETDBKMEigRqBEhkJodHRwOi8vd3d3Lm1pY3Jvc29mdC5jb20vcGtpb3BzL2NybC9NaWNTZWNTZXJDQTIwMTFfMjAxMS0xMC0xOC5jcmwwYAYIKwYBBQUHAQEEVDBSMFAGCCsGAQUFBzAChkRodHRwOi8vd3d3Lm1pY3Jvc29mdC5jb20vcGtpb3BzL2NlcnRzL01pY1NlY1NlckNBMjAxMV8yMDExLTEwLTE4LmNydDANBgkqhkiG9w0BAQsFAAOCAgEAoKKuLorfzJWL6HsBsAMwocM295/IkS5FVTASKTdZsqF9Q0Dvngx5YRMY1ljznNhyUYLXzLFKom2oVHlUmhbgY0zVkK798Mv6MEscMxxiQ9o/s8DxxdCBmnwswg3ERR8Q6RCqclsp8LEGUmQXJiLA5EFZSNMa2qlHQS3LoaEz5saVTvt6UihfwclY/F5MJOtlj+IJyv3lIX5Gdzi5wlCp7gMhOZmwDh2RCvulWT3wMmyz2lNT/vkEb8IJ7oKr+/oj7wPTmCZ0k20wyDIa9QbVBMX0CiotY5RHkHZnzkpi4lWc6f2MXsqMRjP6iyyylWQ1Itn+rKjHeBuLAIfqQWuvfT1kyH5IM6QXQw8DS6Wto0hjIx9epUOPscxOr/Qli8zOYJ3i/h3j9/x41hArCnla/ISf5hDVPm0/LTDfFZWxuvMjjnkk+HmsEpq5oaV/Pmuh8ml47kXWddJrAJGDPtEZNqpjO+ObH0P7kb/t5feK1mTmSsKwMJVTnlIUuubbRM2ZeQ0kkZKSUhVjMvO6YfoR6f2EkrCXWlr9VPYtro+pAy4cVMARDW1aOPPLyxk/7cLL+YUTYbEOw+D+bQXEr00AsjmzucvRN2paejjBSH8A+8k+alPobReH88Ktlo4GkqbK9S3vSqH4zJC3GcIJ+mQBxcUlmKWbC5lRo9btWPcTEOU=\",\"chain\":[\"MIIG2DCCBMCgAwIBAgIKYT+3GAAAAAAABDANBgkqhkiG9w0BAQsFADCBiDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCldhc2hpbmd0b24xEDAOBgNVBAcTB1JlZG1vbmQxHjAcBgNVBAoTFU1pY3Jvc29mdCBDb3Jwb3JhdGlvbjEyMDAGA1UEAxMpTWljcm9zb2Z0IFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IDIwMTEwHhcNMTExMDE4MjI1NTE5WhcNMjYxMDE4MjMwNTE5WjB+MQswCQYDVQQGEwJVUzETMBEGA1UECBMKV2FzaGluZ3RvbjEQMA4GA1UEBxMHUmVkbW9uZDEeMBwGA1UEChMVTWljcm9zb2Z0IENvcnBvcmF0aW9uMSgwJgYDVQQDEx9NaWNyb3NvZnQgU2VjdXJlIFNlcnZlciBDQSAyMDExMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEA0AvApKgZgeI25eKq5fOyFVh1vrTlSfHghPm7DWTvhcGBVbjz5/FtQFU9zotq0YST9XV8W6TUdBDKMvMj067uz54EWMLZR8vRfABBSHEbAWcXGK/G/nMDfuTvQ5zvAXEqH4EmQ3eYVFdznVUr8J6OfQYOrBtU8yb3+CMIIoueBh03OP1y0srlY8GaWn2ybbNSqW7prrX8izb5nvr2HFgbl1alEeW3Utu76fBUv7T/LGy4XSbOoArX35Ptf92s8SxzGtkZN1W63SJ4jqHUmwn4ByIxcbCUruCw5yZEV5CBlxXOYexl4kvxhVIWMvi1eKp+zU3sgyGkqJu+mmoE4KMczVYYbP1rL0I+4jfycqvQeHNye97sAFjlITCjCDqZ75/D93oWlmW1w4Gv9DlwSa/2qfZqADj5tAgZ4Bo1pVZ2Il9q8mmuPq1YRk24VPaJQUQecrG8EidT0sH/ss1QmB619Lu2woI52awb8jsnhGqwxiYL1zoQ57PbfNNWrFNMC/o7MTd02Fkr+QB5GQZ7/RwdQtRBDS8FDtVrSSP/z834eoLP2jwt3+jYEgQYuh6Id7iYHxAHu8gFfgsJv2vd405bsPnHhKY7ykyfW2Ip98eiqJWIcCzlwT88UiNPQJrDMYWDL78p8R1QjyGWB87v8oDCRH2bYu8vw3eJq0VNUz4CedMCAwEAAaO
CAUswggFHMBAGCSsGAQQBgjcVAQQDAgEAMB0GA1UdDgQWBBQ2VollSctbmy88rEIWUE2RuTPXkTAZBgkrBgEEAYI3FAIEDB4KAFMAdQBiAEMAQTALBgNVHQ8EBAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAfBgNVHSMEGDAWgBRyLToCMZBDuRQFTuHqp8cx0SOJNDBaBgNVHR8EUzBRME+gTaBLhklodHRwOi8vY3JsLm1pY3Jvc29mdC5jb20vcGtpL2NybC9wcm9kdWN0cy9NaWNSb29DZXJBdXQyMDExXzIwMTFfMDNfMjIuY3JsMF4GCCsGAQUFBwEBBFIwUDBOBggrBgEFBQcwAoZCaHR0cDovL3d3dy5taWNyb3NvZnQuY29tL3BraS9jZXJ0cy9NaWNSb29DZXJBdXQyMDExXzIwMTFfMDNfMjIuY3J0MA0GCSqGSIb3DQEBCwUAA4ICAQBByGHB9VuePpEx8bDGvwkBtJ22kHTXCdumLg2fyOd2NEavB2CJTIGzPNX0EjV1wnOl9U2EjMukXa+/kvYXCFdClXJlBXZ5re7RurguVKNRB6xo6yEM4yWBws0q8sP/z8K9SRiax/CExfkUvGuV5Zbvs0LSU9VKoBLErhJ2UwlWDp3306ZJiFDyiiyXIKK+TnjvBWW3S6EWiN4xxwhCJHyke56dvGAAXmKX45P8p/5beyXf5FN/S77mPvDbAXlCHG6FbH22RDD7pTeSk7Kl7iCtP1PVyfQoa1fB+B1qt1YqtieBHKYtn+f00DGDl6gqtqy+G0H15IlfVvvaWtNefVWUEH5TV/RKPUAqyL1nn4ThEO792msVgkn8Rh3/RQZ0nEIU7cU507PNC4MnkENRkvJEgq5umhUXshn6x0VsmAF7vzepsIikkrw4OOAd5HyXmBouX+84Zbc1L71/TyH6xIzSbwb5STXq3yAPJarqYKssH0uJ/Lf6XFSQSz6iKE9s5FJlwf2QHIWCiG7pplXdISh5RbAU5QrM5l/Eu9thNGmfrCY498EpQQgVLkyg9/kMPt5fqwgJLYOsrDSDYvTJSUKJJbVuskfFszmgsSAbLLGOBG+lMEkc0EbpQFv0rW6624JKhxJKgAlN2992uQVbG+C7IHBfACXH0w76Fq17Ip5xCA==\",\"MIIF7TCCA9WgAwIBAgIQP4vItfyfspZDtWnWbELhRDANBgkqhkiG9w0BAQsFADCBiDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCldhc2hpbmd0b24xEDAOBgNVBAcTB1JlZG1vbmQxHjAcBgNVBAoTFU1pY3Jvc29mdCBDb3Jwb3JhdGlvbjEyMDAGA1UEAxMpTWljcm9zb2Z0IFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IDIwMTEwHhcNMTEwMzIyMjIwNTI4WhcNMzYwMzIyMjIxMzA0WjCBiDELMAkGA1UEBhMCVVMxEzARBgNVBAgTCldhc2hpbmd0b24xEDAOBgNVBAcTB1JlZG1vbmQxHjAcBgNVBAoTFU1pY3Jvc29mdCBDb3Jwb3JhdGlvbjEyMDAGA1UEAxMpTWljcm9zb2Z0IFJvb3QgQ2VydGlmaWNhdGUgQXV0aG9yaXR5IDIwMTEwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCygEGqNThNE3IyaCJNuLLx/9VSvGzH9dJKjDbu0cJcfoyKrq8TKG/Ac+M6ztAlqFo6be+ouFmrEyNozQwph9FvgFyPRH9dkAFSWKxRxV8qh9zc2AodwQO5e7BW6KPeZGHCnvjzfLnsDbVU/ky2ZU+I8JxImQxCCwl8MVkXeQZ4KI2JOkwDJb5xalwL54RgpJki49KvhKSn+9GY7Qyp3pSJ4Q6g3MDOmT3qCFK7VnnkH4S6Hri0xElcTzFLh93dBWcmmYDgcRGjuKVB4qRTufcyKYMME782XgSzS0NHL2vikR7TmE/dQgfI6B0S/Jmpaz6SfsjWaTr8ZL22CZ3K/QwLopt3YEsDlKQwaRLWQi3BQUzK3Kr9j1uDRprZ/LHR47PJf0h6zSTwQY9cdNCssBAgBkm3xy0hyFfj0IbzA2j70M5xwYmZSmQBbP3sMJHPQTySx+W6hh1hhMdfgzlirrSSL0fzC/hV66AfWdC7dJse0Hbm8ukG1xDo+mTeacY1logC8Ea4PyeZb8txiSk190gWAjWP1Xl8TQLPX+uKg09FcYj5qQ1OcunCnAfPSRtOBA5jUYxe2ADBVSy2xuDCZU7JNDn1nLPEfuhhbhNfFcRf2X7tHc7uROzLLoax7Dj2cO2rXBPB2Q8Nx4CyVe0096yb5MPa50c8prWPMd/FS6/r8QIDAQABo1EwTzALBgNVHQ8EBAMCAYYwDwYDVR0TAQH/BAUwAwEB/zAdBgNVHQ4EFgQUci06AjGQQ7kUBU7h6qfHMdEjiTQwEAYJKwYBBAGCNxUBBAMCAQAwDQYJKoZIhvcNAQELBQADggIBAH9yzw+3xRXbm8BJyiZb/p4T5tPw0tuXX/JLP02zrhmu7deXoKzvqTqjwkGw5biRnhOBJAPmCf0/V0A5ISRW0RAvS0CpNoZLtFNXmvvxfomPEf4YbFGq6O0JlbXlccmh6Yd1phV/yX43VF50k8XDZ8wNT2uoFwxtCJJ+i92Bqi1wIcM9BhS7vyRep4TXPw8hIr1LAAbblxzYXtTFC1yHblCk6MM4pPvLLMWSZpuFXst6bJN8gClYW1e1QGm6CHmmZGIVnYeWRbVmIyADixxzoNOieTPgUFmG2y/lAiXqcyqfABTINseSO+lOAOzYVgm5M0kS0lQLAausR7aRKX1MtHWAUgHoyoL2n8ysnI8X6i8msKtyrAv+nlEex0NVZ09Rs1fWtuzuUrc66U7h14GIvE+OdbtLqPA1qibUZ2dJsnBMO5PcHd94kIZysjik0dySTclY6ysSXNQ7roxrsIPlAT/4CTL2kzU0Iq/dNw13CYArzUgA8YyZGUcFAenRv9FO0OYoQzeZpApKCNmacXPSqs0xE2N2oTdvkjgefRI8ZjLny23h/FKJ3crWZgWalmG+oijHHKOnNlA8OqTfSm7mhzvO6/DggTedEzxSjr25HTTGHdUKaj2YKXCMiSrRq4IQSB/c9O+lxbtVGjhjhE63bK2VVOxlIhBJF7jAHscPrFRH\"]}" > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% NEQ 0 (
set "errorDenoscription=Unable to write onboarding information to registry."
set errorCode=10
set lastError=%ERRORLEVEL%
GOTO ERROR
)
echo Starting the service, if not already running
echo.
sc query "SENSE" | find /i "RUNNING" >NUL 2>&1
if %ERRORLEVEL% EQU 0 GOTO RUNNING
net start sense > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% NEQ 0 (
echo Microsoft Defender for Endpoint Service has not started yet
GOTO WAIT_FOR_THE_SERVICE_TO_START
)
goto SUCCEEDED
:RUNNING
set "runningOutput=The Microsoft Defender for Endpoint Service is already running!"
echo %runningOutput%
echo.
eventcreate /l Application /so WDATPOnboarding /t Information /id 10 /d "%runningOutput%" >NUL 2>&1
GOTO WAIT_FOR_THE_SERVICE_TO_START
:ERROR
if %ERRORLEVEL% NEQ 0 (
set "errorDenoscription=Unable to write onboarding information to registry."
set errorCode=10
set lastError=%ERRORLEVEL%
GOTO ERROR
)
echo Starting the service, if not already running
echo.
sc query "SENSE" | find /i "RUNNING" >NUL 2>&1
if %ERRORLEVEL% EQU 0 GOTO RUNNING
net start sense > %TMP%\senseTmp.txt 2>&1
if %ERRORLEVEL% NEQ 0 (
echo Microsoft Defender for Endpoint Service has not started yet
GOTO WAIT_FOR_THE_SERVICE_TO_START
)
goto SUCCEEDED
:RUNNING
set "runningOutput=The Microsoft Defender for Endpoint Service is already running!"
echo %runningOutput%
echo.
eventcreate /l Application /so WDATPOnboarding /t Information /id 10 /d "%runningOutput%" >NUL 2>&1
GOTO WAIT_FOR_THE_SERVICE_TO_START
:ERROR
Set /P errorMsg=<%TMP%\senseTmp.txt
set "errorOutput=[Error Id: %errorCode%, Error Level: %lastError%] %errorDenoscription% Error message: %errorMsg%"
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type 'using System; using System.Diagnostics; using System.Diagnostics.Tracing; namespace Sense { [EventData(Name = \"Onboarding\")]public struct Onboarding{public string Message { get; set; }} public class Trace {public static EventSourceOptions TelemetryCriticalOption = new EventSourceOptions(){Level = EventLevel.Error, Keywords = (EventKeywords)0x0000200000000000, Tags = (EventTags)0x0200000}; public void WriteOnboardingMessage(string message){es.Write(\"OnboardingScript\", TelemetryCriticalOption, new Onboarding {Message = message});} private static readonly string[] telemetryTraits = { \"ETW_GROUP\", \"{5ECB0BAC-B930-47F5-A8A4-E8253529EDB7}\" }; private EventSource es = new EventSource(\"Microsoft.Windows.Sense.Client.Management\",EventSourceSettings.EtwSelfDescribingEventFormat,telemetryTraits);}}'; $logger = New-Object -TypeName Sense.Trace; $logger.WriteOnboardingMessage('%errorOutput%')" >NUL 2>&1
echo %errorOutput%
echo %troubleshootInfo%
echo.
eventcreate /l Application /so WDATPOnboarding /t Error /id %errorCode% /d "%errorOutput%" >NUL 2>&1
GOTO CLEANUP
:SUCCEEDED
echo Finished performing onboarding operations
echo.
GOTO WAIT_FOR_THE_SERVICE_TO_START
:WAIT_FOR_THE_SERVICE_TO_START
echo Waiting for the service to start
echo.
set /a counter=0
:SENSE_RUNNING_WAIT
sc query "SENSE" | find /i "RUNNING" >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
set "errorDenoscription=Unable to start Microsoft Defender for Endpoint Service."
set errorCode=15
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_RUNNING_WAIT
)
set /a counter=0
:SENSE_ONBOARDED_STATUS_WAIT
REG query "HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status" /v OnboardingState /reg:64 >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
@echo Microsoft Defender for Endpoint Service is not running as expected> %TMP%\senseTmp.txt
set errorCode=35
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_ONBOARDED_STATUS_WAIT
)
set /a counter=0
:SENSE_ONBOARDED_WAIT
REG query "HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status" /v OnboardingState /reg:64 | find /i "0x1" >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
@echo Microsoft Defender for Endpoint Service is not running as expected> %TMP%\senseTmp.txt
set errorCode=40
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_ONBOARDED_WAIT
)
set "successOutput=Successfully onboarded machine to Microsoft Defender for Endpoint"
echo %successOutput%
echo.
eventcreate /l Application /so WDATPOnboarding /t Information /id 20 /d "%successOutput%" >NUL 2>&1
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type 'using System; using System.Diagnostics; using System.Diagnostics.Tracing; namespace Sense { [EventData(Name = \"Onboarding\")]public struct Onboarding{public string Message { get; set; }} public class Trace {public static EventSourceOptions TelemetryCriticalOption = new EventSourceOptions(){Level = EventLevel.Informational, Keywords = (EventKeywords)0x0000200000000000, Tags = (EventTags)0x0200000}; public void WriteOnboardingMessage(string message){es.Write(\"OnboardingScript\", TelemetryCriticalOption, new Onboarding {Message = message});} private static readonly string[] telemetryTraits = { \"ETW_GROUP\", \"{5ECB0BAC-B930-47F5-A8A4-E8253529EDB7}\" }; private EventSource es = new
set "errorOutput=[Error Id: %errorCode%, Error Level: %lastError%] %errorDenoscription% Error message: %errorMsg%"
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type 'using System; using System.Diagnostics; using System.Diagnostics.Tracing; namespace Sense { [EventData(Name = \"Onboarding\")]public struct Onboarding{public string Message { get; set; }} public class Trace {public static EventSourceOptions TelemetryCriticalOption = new EventSourceOptions(){Level = EventLevel.Error, Keywords = (EventKeywords)0x0000200000000000, Tags = (EventTags)0x0200000}; public void WriteOnboardingMessage(string message){es.Write(\"OnboardingScript\", TelemetryCriticalOption, new Onboarding {Message = message});} private static readonly string[] telemetryTraits = { \"ETW_GROUP\", \"{5ECB0BAC-B930-47F5-A8A4-E8253529EDB7}\" }; private EventSource es = new EventSource(\"Microsoft.Windows.Sense.Client.Management\",EventSourceSettings.EtwSelfDescribingEventFormat,telemetryTraits);}}'; $logger = New-Object -TypeName Sense.Trace; $logger.WriteOnboardingMessage('%errorOutput%')" >NUL 2>&1
echo %errorOutput%
echo %troubleshootInfo%
echo.
eventcreate /l Application /so WDATPOnboarding /t Error /id %errorCode% /d "%errorOutput%" >NUL 2>&1
GOTO CLEANUP
:SUCCEEDED
echo Finished performing onboarding operations
echo.
GOTO WAIT_FOR_THE_SERVICE_TO_START
:WAIT_FOR_THE_SERVICE_TO_START
echo Waiting for the service to start
echo.
set /a counter=0
:SENSE_RUNNING_WAIT
sc query "SENSE" | find /i "RUNNING" >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
set "errorDenoscription=Unable to start Microsoft Defender for Endpoint Service."
set errorCode=15
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_RUNNING_WAIT
)
set /a counter=0
:SENSE_ONBOARDED_STATUS_WAIT
REG query "HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status" /v OnboardingState /reg:64 >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
@echo Microsoft Defender for Endpoint Service is not running as expected> %TMP%\senseTmp.txt
set errorCode=35
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_ONBOARDED_STATUS_WAIT
)
set /a counter=0
:SENSE_ONBOARDED_WAIT
REG query "HKLM\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status" /v OnboardingState /reg:64 | find /i "0x1" >NUL 2>&1
if %ERRORLEVEL% NEQ 0 (
IF %counter% EQU 4 (
@echo Microsoft Defender for Endpoint Service is not running as expected> %TMP%\senseTmp.txt
set errorCode=40
set lastError=%ERRORLEVEL%
GOTO ERROR
)
set /a counter=%counter%+1
timeout 5 >NUL 2>&1
GOTO :SENSE_ONBOARDED_WAIT
)
set "successOutput=Successfully onboarded machine to Microsoft Defender for Endpoint"
echo %successOutput%
echo.
eventcreate /l Application /so WDATPOnboarding /t Information /id 20 /d "%successOutput%" >NUL 2>&1
%powershellPath% -ExecutionPolicy Bypass -NoProfile -Command "Add-Type 'using System; using System.Diagnostics; using System.Diagnostics.Tracing; namespace Sense { [EventData(Name = \"Onboarding\")]public struct Onboarding{public string Message { get; set; }} public class Trace {public static EventSourceOptions TelemetryCriticalOption = new EventSourceOptions(){Level = EventLevel.Informational, Keywords = (EventKeywords)0x0000200000000000, Tags = (EventTags)0x0200000}; public void WriteOnboardingMessage(string message){es.Write(\"OnboardingScript\", TelemetryCriticalOption, new Onboarding {Message = message});} private static readonly string[] telemetryTraits = { \"ETW_GROUP\", \"{5ECB0BAC-B930-47F5-A8A4-E8253529EDB7}\" }; private EventSource es = new
EventSource(\"Microsoft.Windows.Sense.Client.Management\",EventSourceSettings.EtwSelfDescribingEventFormat,telemetryTraits);}}'; $logger = New-Object -TypeName Sense.Trace; $logger.WriteOnboardingMessage('%successOutput%')" >NUL 2>&1
"%PROGRAMFILES%\Windows Defender\MpCmdRun.exe" -ReloadEngine >NUL 2>&1
GOTO CLEANUP
:CLEANUP
if exist %TMP%\senseTmp.txt del %TMP%\senseTmp.txt
pause
EXIT /B %errorCode%
https://redd.it/11qxe60
@r_bash
"%PROGRAMFILES%\Windows Defender\MpCmdRun.exe" -ReloadEngine >NUL 2>&1
GOTO CLEANUP
:CLEANUP
if exist %TMP%\senseTmp.txt del %TMP%\senseTmp.txt
pause
EXIT /B %errorCode%
https://redd.it/11qxe60
@r_bash
Reddit
r/bash on Reddit: My manager told me to execute this without any explenation on what it does. Anyone here has a clue?
Posted by u/ya-boi-moe - No votes and no comments
I made a bash noscript to fetch all Android System Info in the termux app, Any Suggestions can be helpful to improve the noscript.
https://redd.it/11r1x2y
@r_bash
https://redd.it/11r1x2y
@r_bash
Reddit
r/bash on Reddit: I made a bash noscript to fetch all Android System Info in the termux app, Any Suggestions can be helpful to improve…
Posted by u/A_J07 - No votes and no comments
While (loop) with if-statement and timeout after 300 seconds
Hi,
I want to create a while (loop) with an if-statement which timesout after 300 seconds, when the neccessary value isnt provided from the service.
My attempt:
Note:
Im executing a curl command to get a value from the backend service. If "1.0" then stop while-loop, if the service isnt reachable for example "120 seconds" wait and then proceed.
https://redd.it/11r91rv
@r_bash
Hi,
I want to create a while (loop) with an if-statement which timesout after 300 seconds, when the neccessary value isnt provided from the service.
My attempt:
# API Request (GET) - Status
API_STATUS=`curl .....`
# Set timeout value
TIMEOUT=0
while [[ "$API_STATUS" != "1.0" ]];
do
# Increase timeout value by 1
TIMEOUT=$((TIMEOUT+1))
if [[ TIMEOUT != "60" ]]
then
# Wait 5 seconds
sleep 5
API_STATUS=`curl .....`
elif [[ TIMEOUT == "60" ]]
then
echo "$TIMESTAMP Not reachable." >> $LOG
exit
fi
done
Note:
Im executing a curl command to get a value from the backend service. If "1.0" then stop while-loop, if the service isnt reachable for example "120 seconds" wait and then proceed.
https://redd.it/11r91rv
@r_bash
Reddit
r/bash on Reddit: While (loop) with if-statement and timeout after 300 seconds
Posted by u/HeyWatchOutDude - No votes and 1 comment
Code golf: highly minified function for injecting ANSI color in bash noscripts
I've been putting together a function for inserting ANSI color sequences in bash noscripts and trying to keep the character count down.
Here's a picture to give you an idea what I'm going for: https://i.imgur.com/6CnnGtN.png
The idea is to replace all those ubiquitous color definition blocks in the noscripts I inherit that leave the first page looking like this (clipped from a recent submission here):
#Regular Color Variables
coff='\033[0m' #No Color
black='\033[0;30m' #Black
red='\033[1;91m' #Red
green='\033[1;92m' #Green
yellow='\033[0;93m' #Yellow
blue='\033[0;94m' #Blue
purple='\033[0;95m' #Purple
cyan='\033[0;96m' #Cyan
white='\033[0;97m' #White
#BackGround Colors Variables
bblack='\03340m'
b_red='\033[41m'
b_green='\033[42m'
b_yellow='\033[43m'
b_blue='\033[44m'
b_purple='\033[95m'
b_cyan='\033[46m'
b_white='\033[47m'
I've got something that supports all 16 colors on all 16 background colors in the standard 4-bit ANSI palette, as well as bold, underline, and "terminal default" codes (`\e[39m`, `\e[49m`).
clr() {
local in="$*" fgb=30 bgb=40 colors="krgybmcw =" fg bg cs
[[ "$in" ] || { printf "%b" "\e0m"; return; } # reset
[[ "$in" == *-* ] && cs=";22;24"; # normal
[ "$in" == *+* ] && cs=";1"; # bold
[ "$in" == *_* ] && cs+=";4"; # underline
in=${in//-_+ /}
[ "${in,,}" =~ ^[.=rgbcmykw{0,2}$ ]] || return 1
fg=${in:0:1}; [ "$fg" ] || fg=.; bg=${in:1:1}; bg=${bg#.}
[ "$fg" =~ [A-Z ]] && fgb=90
[ "$bg" =~ [A-Z ]] && bgb=100
[ "$fg" == "." ] || { i=${colors%%"${fg,,}"}; cs+=";$((${#i}+fgb))"; }
[[ "$bg" ]] && { i=${colors%%"${bg,,}"}; cs+=";$((${#i}+bgb))"; }
printf "%b" "\e${cs#;}m"
}
I'm trying to keep it mostly minified so it's a tricky read. The less obvious abbreviations are `in`: input arguments, `cs`: control sequence, `fgb`/`bgb`: foreground/background brightness.
`shellcheck --shell=bash clr.sh` surprisingly had no complaints when I fed it this snippet, I was expecting to be flooded with complaints (so many unquoted expansions and assignments!) so I'm not even sure I'm using it right.
The parameters it accepts:
Parameter | Result
---|---
no arguments | Reset to default formatting
r,g,b,c,m,y,k,w | Red, green, blue, cyan, magenta, yellow, black, white
R,G,B,C,M,Y,K,W | Bright versions of same colors
+ | bold
_ | underline
- | strip formatting (bold/underline)
= | terminal default background/foreground
. | placeholder to separate foreground from background when changing background only
It doesn't care about the order of parameters or the spacing, except that the background color must be preceded by a foreground color (hence the no-op `.` placeholder for leaving foreground alone).
I'm trying to make it so that it outputs the minimal escape sequence for the desired formatting: e.g. no `0;` or `1;` when changing only the color. What I most dissatisfied with so far is having to use `22;24` to strip the bold/underline formatting, but `0;` strips the colors along with the formatting (breaking the "Blue bold not bold" example in the screenshot) and I don't want to make the function have to track any state to know whether it's underlining or bold that needs to be cancelled out.
Any tips? Especially ones that reduce the character count!
[https://redd.it/11ri7f3
@r_bash
I've been putting together a function for inserting ANSI color sequences in bash noscripts and trying to keep the character count down.
Here's a picture to give you an idea what I'm going for: https://i.imgur.com/6CnnGtN.png
The idea is to replace all those ubiquitous color definition blocks in the noscripts I inherit that leave the first page looking like this (clipped from a recent submission here):
#Regular Color Variables
coff='\033[0m' #No Color
black='\033[0;30m' #Black
red='\033[1;91m' #Red
green='\033[1;92m' #Green
yellow='\033[0;93m' #Yellow
blue='\033[0;94m' #Blue
purple='\033[0;95m' #Purple
cyan='\033[0;96m' #Cyan
white='\033[0;97m' #White
#BackGround Colors Variables
bblack='\03340m'
b_red='\033[41m'
b_green='\033[42m'
b_yellow='\033[43m'
b_blue='\033[44m'
b_purple='\033[95m'
b_cyan='\033[46m'
b_white='\033[47m'
I've got something that supports all 16 colors on all 16 background colors in the standard 4-bit ANSI palette, as well as bold, underline, and "terminal default" codes (`\e[39m`, `\e[49m`).
clr() {
local in="$*" fgb=30 bgb=40 colors="krgybmcw =" fg bg cs
[[ "$in" ] || { printf "%b" "\e0m"; return; } # reset
[[ "$in" == *-* ] && cs=";22;24"; # normal
[ "$in" == *+* ] && cs=";1"; # bold
[ "$in" == *_* ] && cs+=";4"; # underline
in=${in//-_+ /}
[ "${in,,}" =~ ^[.=rgbcmykw{0,2}$ ]] || return 1
fg=${in:0:1}; [ "$fg" ] || fg=.; bg=${in:1:1}; bg=${bg#.}
[ "$fg" =~ [A-Z ]] && fgb=90
[ "$bg" =~ [A-Z ]] && bgb=100
[ "$fg" == "." ] || { i=${colors%%"${fg,,}"}; cs+=";$((${#i}+fgb))"; }
[[ "$bg" ]] && { i=${colors%%"${bg,,}"}; cs+=";$((${#i}+bgb))"; }
printf "%b" "\e${cs#;}m"
}
I'm trying to keep it mostly minified so it's a tricky read. The less obvious abbreviations are `in`: input arguments, `cs`: control sequence, `fgb`/`bgb`: foreground/background brightness.
`shellcheck --shell=bash clr.sh` surprisingly had no complaints when I fed it this snippet, I was expecting to be flooded with complaints (so many unquoted expansions and assignments!) so I'm not even sure I'm using it right.
The parameters it accepts:
Parameter | Result
---|---
no arguments | Reset to default formatting
r,g,b,c,m,y,k,w | Red, green, blue, cyan, magenta, yellow, black, white
R,G,B,C,M,Y,K,W | Bright versions of same colors
+ | bold
_ | underline
- | strip formatting (bold/underline)
= | terminal default background/foreground
. | placeholder to separate foreground from background when changing background only
It doesn't care about the order of parameters or the spacing, except that the background color must be preceded by a foreground color (hence the no-op `.` placeholder for leaving foreground alone).
I'm trying to make it so that it outputs the minimal escape sequence for the desired formatting: e.g. no `0;` or `1;` when changing only the color. What I most dissatisfied with so far is having to use `22;24` to strip the bold/underline formatting, but `0;` strips the colors along with the formatting (breaking the "Blue bold not bold" example in the screenshot) and I don't want to make the function have to track any state to know whether it's underlining or bold that needs to be cancelled out.
Any tips? Especially ones that reduce the character count!
[https://redd.it/11ri7f3
@r_bash
aliases to save current dir in one terminal and move to it in a different terminal
I often open a new terminal windows to work in the same directory as my current terminal window and I find it annoying to have to manually cd to it, specially if current directory path is long. There is probably a better way but here is what I came up with:
sf is for save folder, lf for load folder.
I literally just came up with that so I haven't really used it for real beyond testing.
https://redd.it/11rjw8q
@r_bash
I often open a new terminal windows to work in the same directory as my current terminal window and I find it annoying to have to manually cd to it, specially if current directory path is long. There is probably a better way but here is what I came up with:
alias sf='pwd > ~/.folder'alias lf='cd "$(cat ~/.folder)"'sf is for save folder, lf for load folder.
I literally just came up with that so I haven't really used it for real beyond testing.
https://redd.it/11rjw8q
@r_bash
Reddit
r/bash on Reddit: aliases to save current dir in one terminal and move to it in a different terminal
Posted by u/Frankmc2 - No votes and 1 comment
Read contents of file and run a command
My scenario:
cat filesystems.txt
#path;major;minor;average
/var;10;10;10
/opt;10;10;10
Then, my bash must read this file (filesystems.txt) and for each line of this file (except first line), do "df -h" for each item.
My goal is to have this:
df -h /var
df -h /opt
​
https://redd.it/11rl8b0
@r_bash
My scenario:
cat filesystems.txt
#path;major;minor;average
/var;10;10;10
/opt;10;10;10
Then, my bash must read this file (filesystems.txt) and for each line of this file (except first line), do "df -h" for each item.
My goal is to have this:
df -h /var
df -h /opt
​
https://redd.it/11rl8b0
@r_bash
Reddit
r/bash on Reddit: Read contents of file and run a command
Posted by u/BlueAcronis - No votes and no comments
having trouble checking if a drive is mounted!
Greetings everyone,
​
I'm making a little wrapper for pmount to automate the mounting/dismounting of hotplugged LUKS USB devices. I'll post the noscript below.
https://pastebin.com/Tr9ZUEJe
I'm having trouble in particular with the "scan" function. I'm trying to get it to display eligable devices ONLY if they are not already currently mounted. I'm not sure how to do this. Currently, it displays (correctly) all devices which 1.) have a UUID and 2.) have an associated .key file in the $SECRETSDIR/luks folder. I'd like this output to exclude whatever is included in the "currentlymounted" array.
​
I'd really value any input about how to accomplish this, thanks in advance!
https://redd.it/11rk4b0
@r_bash
Greetings everyone,
​
I'm making a little wrapper for pmount to automate the mounting/dismounting of hotplugged LUKS USB devices. I'll post the noscript below.
https://pastebin.com/Tr9ZUEJe
I'm having trouble in particular with the "scan" function. I'm trying to get it to display eligable devices ONLY if they are not already currently mounted. I'm not sure how to do this. Currently, it displays (correctly) all devices which 1.) have a UUID and 2.) have an associated .key file in the $SECRETSDIR/luks folder. I'd like this output to exclude whatever is included in the "currentlymounted" array.
​
I'd really value any input about how to accomplish this, thanks in advance!
https://redd.it/11rk4b0
@r_bash
Pastebin
#!/bin/bash# This noscript is essentially an automated pmount tool which allows - Pastebin.com
Pastebin.com is the number one paste tool since 2002. Pastebin is a website where you can store text online for a set period of time.
Emulate "Copy Link To Clipboard" By Copying Text Wrapper - How To?
Is it possible to do the copying in bash by emulating "copy link to clipboard" when the text wrapper is highlighted? Projecting this onto Markdown format of URL it would look like highlighting the
https://i.imgur.com/AvTIOaM.png
https://redd.it/11rjkpg
@r_bash
Is it possible to do the copying in bash by emulating "copy link to clipboard" when the text wrapper is highlighted? Projecting this onto Markdown format of URL it would look like highlighting the
[reddit!] segment of [reddit](https://reddit.com) with (https://reddit.com) going to the clipboard. Refer to the linked image for the visual example.https://i.imgur.com/AvTIOaM.png
https://redd.it/11rjkpg
@r_bash
smenu is so cool! :)
A demo of what kind of menus you can make with
smenu demo
https://redd.it/11rrfcs
@r_bash
A demo of what kind of menus you can make with
smenu, and a small tour of the command line history too, which I have installed on Ctrl-n, since I have FZF on Ctrl-r.smenu demo
https://redd.it/11rrfcs
@r_bash
asciinema.org
smenu is so cool!
Recorded by McUsr
My VOIP phone service provides an API to send SMS .. is this how its done using curl
API is
https://www.thevoipcompany.com/send-sms?username=username&password=password&to=destination&subnoscriptionId=subnoscription ID&text=message
My understanding curl could do this with something like this ... correct?
>curl -X POST -d 'username=username&password=password&to=destination&subnoscriptionId=subnoscription id&text=message' https://www.mynetfone.com.au/send-sms
If correct it would be simple to put it into a bash wrapper.
https://redd.it/11rved7
@r_bash
API is
https://www.thevoipcompany.com/send-sms?username=username&password=password&to=destination&subnoscriptionId=subnoscription ID&text=message
My understanding curl could do this with something like this ... correct?
>curl -X POST -d 'username=username&password=password&to=destination&subnoscriptionId=subnoscription id&text=message' https://www.mynetfone.com.au/send-sms
If correct it would be simple to put it into a bash wrapper.
https://redd.it/11rved7
@r_bash
Bash continuous parallelization
I work with academic research, specifically with simulations. The important feature of these simulations in the context of the problem is that some of them take longer than others.
I want to run let's say 1000 simulations, each in a single thread of the processador. If my machine has 6 threads i can do several batches of 6 + one batch of the remaining.
Using something like:
And that's definetly runs faster than doing one by one, sequentially. But if i have at least process that takes a lot longer than the others, i'm losing precious time.
The final question is: Is there a simple way that can i set a fixed number of processes to be running at the same time, and as soon as one is finishes another one takes it place, that way i'm not bottlenecked by a single slower program.
I will greatly apreciate the help, since solving this would greatly improve my reseach.
https://redd.it/11rxgwt
@r_bash
I work with academic research, specifically with simulations. The important feature of these simulations in the context of the problem is that some of them take longer than others.
I want to run let's say 1000 simulations, each in a single thread of the processador. If my machine has 6 threads i can do several batches of 6 + one batch of the remaining.
Using something like:
./run.out 1 & ./run.out 2 & ./run.out 3 & ./run.out 4 & ./run.out 5 & ./run.out 6 & wait ./run.out 7 & ./run.out 8 & ./run.out 9 & ./run.out 9 & ./run.out 10 & ./run.out 11 & wait And that's definetly runs faster than doing one by one, sequentially. But if i have at least process that takes a lot longer than the others, i'm losing precious time.
The final question is: Is there a simple way that can i set a fixed number of processes to be running at the same time, and as soon as one is finishes another one takes it place, that way i'm not bottlenecked by a single slower program.
I will greatly apreciate the help, since solving this would greatly improve my reseach.
https://redd.it/11rxgwt
@r_bash
Reddit
r/bash on Reddit: Bash continuous parallelization
Posted by u/Farinha96br - No votes and 1 comment